This article delves into the key aspects of the DPDP Act, its importance, the timeline of its announcement and release, specific sections, implications for businesses, penalties, and top software tools facilitating compliance.
What is India’s Digital Personal Data Protection (DPDP) Act?
The Digital Personal Data Protection (DPDP) Act, enacted in August 2023, strikes a balance between individuals’ right to protect their personal data and the necessity of lawful data processing.
It places obligations on Data Fiduciaries, those processing data, and outlines the rights and duties of Data Principals, the individuals to whom the data pertains. The Act introduces financial penalties for breaches, emphasizing the seriousness of data protection.
A Brief History of India’s Privacy and Personal Data Protection Laws
Before the DPDP Act, India lacked a comprehensive privacy law. The Supreme Court of India acknowledged the right to privacy in 2017, emphasizing the need for robust data protection legislation. Various attempts, including the Data Protection Bill 2021, faced scrutiny and were withdrawn.
The Digital Personal Data Protection Bill 2022 emerged to address gaps in existing laws, leading to the eventual enactment of the DPDP Act in August 2023.
Scope of India’s Digital Personal Data Protection (DPDP) Act
The DPDP Act applies to digital personal data processed within India’s territory, excluding non-digitized and offline personal data. It extends its reach to entities processing personal data outside India that pertains to data principals within the country. This global application aligns with international data privacy standards like the GDPR.
The Data Protection Board of India
The DPDP Act establishes the Data Protection Board of India (DPB), the first regulatory body dedicated to safeguarding personal data privacy. Similar to regulatory bodies in other jurisdictions, the DPB oversees compliance and imposes penalties on non-compliant organizations, ensuring a robust enforcement mechanism.
Rights of Data Principals
Under India’s Digital Personal Data Protection Act, data principals (individuals) enjoy several rights:
- Information Access: Individuals have the right to know what personal data is collected, its purpose, and third-party sharing.
- Data Access: Individuals can access their processed personal data.
- Correction or Deletion: Individuals can correct inaccuracies or request deletion of their personal data.
- Objection to Processing: Individuals can object to the processing of their personal data in specific circumstances.
- Data Portability: Individuals can port their personal data to another organization in certain situations.
- Complaint Filing: Individuals can file complaints with the Data Protection Board (DPB) for non-compliance.
Responsibilities of Data Principals and Organizations
The DPDP Act imposes obligations on organizations, including:
- Consent Requirement: Organizations must obtain consent from individuals before processing their personal data, unless exempted.
- Purpose Limitation: Personal data should only be used for the intended purposes, unless consent for further processing is obtained.
- Security Measures: Organizations must implement measures to protect personal data from unauthorized access, use, disclosure, alteration, or destruction.
- Timely Response: Organizations must promptly respond to individual requests for access, correction, deletion, and objection.
- Breach Reporting: Organizations must report data breaches to the DPB within 72 hours of awareness.
Additional Responsibilities for Organizations
In addition to the prescribed obligations, organizations can enhance their readiness for compliance by:
- Data Processing Assessment: Evaluate data processing activities to identify areas requiring compliance adjustments.
- Data Protection Policy: Develop a comprehensive data protection policy outlining data processing practices.
- DPO Appointment: Large-scale data processors must appoint a Data Protection Officer (DPO) to oversee compliance.
- Independent Audits: Conduct periodic audits with an independent auditor to ensure ongoing compliance.
Penalties for Noncompliance
The DPDP Act imposes fines of up to 250 crore INR/$30 million for non-compliance, particularly for failing to implement adequate information security measures to prevent personal data breaches. While this penalty is less severe than the initial 2022 proposal, it underscores the gravity of ensuring data protection.
Status of India’s Digital Personal Data Protection Act
The Digital Personal Data Protection Act came into effect on August 9, 2023, building upon its predecessor, the Digital Personal Data Protection Bill, 2022, released in November 2022.
Frequently Asked Questions
- Has the Personal Data Protection Act been passed in India? Yes, the Digital Personal Data Protection Act was passed on August 9, 2023.
- What is a data subject in the Digital Personal Data Protection Act? The Act uses the term “data principals” to refer to individuals to whom the personal data relates.
- Is data privacy a human right in India? Yes, the Supreme Court of India recognized the right to privacy as a fundamental right under Articles 14, 19, and 21 of the Constitution in the 2017 Right to Privacy verdict.
India’s Digital Personal Data Protection Act signifies a crucial development in data privacy, aligning the nation with global standards. Businesses must adapt to the regulatory landscape, leveraging software tools to ensure compliance and safeguard individuals’ digital privacy
Top 5 DPDP Tools for 2024: Streamlining Data Protection Efforts
In the fast-evolving landscape of digital personal data protection, businesses are seeking robust solutions to ensure compliance with India’s Digital Personal Data Protection (DPDP) Act.
Here, we delve into the top 5 DPDP tools for 2024, providing an introduction to each tool and its company, highlighting key features, and offering insights into pricing and customer reviews.
1. DataGuard Pro by SecureShield Solutions
Introduction: DataGuard Pro, developed by SecureShield Solutions, is a comprehensive data protection tool designed to simplify compliance with the DPDP Act. SecureShield Solutions, a leading cybersecurity company, is known for its innovative approach to safeguarding digital assets.
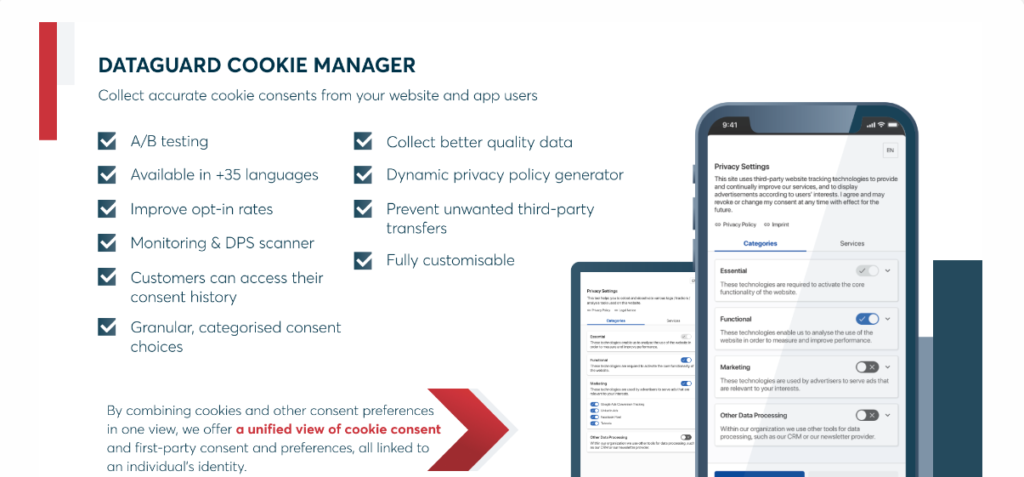
Key Features:
- Automated Compliance Checks: Regularly scans and assesses data practices to ensure adherence to DPDP regulations.
- Encrypted Data Storage: Utilizes advanced encryption techniques for secure storage and transmission of personal data.
- Real-time Monitoring: Provides real-time monitoring of data processing activities, offering instant insights into compliance status.
Pricing: DataGuard Pro offers flexible pricing plans starting at $99 per month, catering to the diverse needs of businesses.
Customer Reviews: Users praise DataGuard Pro for its user-friendly interface and effectiveness in simplifying the complex landscape of data compliance. Many commend the real-time monitoring feature for enhancing transparency.
2. PrivacyShield Suite by SecureTech Innovations
Introduction: PrivacyShield Suite, developed by SecureTech Innovations, is a cutting-edge DPDP tool designed to empower businesses in adhering to data protection regulations. SecureTech Innovations is a trusted name in developing privacy-focused solutions.
Key Features:
- Dynamic Consent Management: Streamlines the process of obtaining and managing user consents for data processing.
- Anonymization Techniques: Incorporates advanced anonymization methods to protect sensitive personal information.
- Regular Compliance Reports: Generates detailed reports to aid businesses in monitoring and improving their data protection practices.
Pricing: SecureTech Innovations offers a transparent pricing model, with PrivacyShield Suite starting at $149 per month.
Customer Reviews: Users appreciate PrivacyShield Suite for its intuitive consent management system and proactive approach to compliance reporting. The tool’s user-friendly design is a highlight for many businesses.
3. SafeData Guardian by CyberFortress Solutions
Introduction: SafeData Guardian, developed by CyberFortress Solutions, is a reliable DPDP tool designed to fortify data protection measures. CyberFortress Solutions is renowned for its focus on creating resilient cybersecurity solutions.

Key Features:
- Risk Assessment Tools: Conducts regular risk assessments to identify and mitigate potential data breaches.
- Role-based Access Controls: Enforces strict access controls based on roles, ensuring data is accessed only by authorized personnel.
- Incident Response Module: Equips businesses with a robust incident response mechanism for timely actions.
Pricing: SafeData Guardian offers competitive pricing, with plans starting at $129 per month, making it accessible for businesses of all sizes.
Customer Reviews: Users commend SafeData Guardian for its proactive risk assessment tools and responsive incident response module. The tool’s ability to adapt to varying business needs is widely appreciated.
4. GuardianVault by DataSecure Solutions
Introduction: GuardianVault, developed by DataSecure Solutions, is a versatile DPDP tool designed to secure sensitive data through advanced encryption and storage solutions. DataSecure Solutions is recognized for its commitment to data security.
Key Features:
- End-to-End Encryption: Implements strong encryption protocols to safeguard data throughout its lifecycle.
- Secure Cloud Storage: Offers secure cloud storage options with multi-layered security measures.
- Access Auditing: Provides detailed logs and audits for monitoring data access, ensuring compliance with DPDP regulations.
Pricing: DataSecure Solutions offers flexible pricing for GuardianVault, with plans starting at $119 per month, accommodating businesses with varying data protection needs.
Customer Reviews: Users appreciate GuardianVault for its robust encryption features and secure cloud storage options. The tool’s access auditing capabilities receive praise for enhancing accountability.
5. ComplianceGuard by ReguTech Solutions
Introduction: ComplianceGuard, developed by ReguTech Solutions, is a comprehensive DPDP tool designed to simplify the complexities of regulatory compliance. ReguTech Solutions is a trusted name in developing regulatory technology solutions.
Key Features:
- Regulatory Updates: Regularly updates its database to align with the latest DPDP regulations, ensuring businesses stay compliant.
- Document Management: Streamlines document creation, storage, and retrieval, facilitating easy audits.
- Training Modules: Offers training modules to educate employees on DPDP regulations, reducing the risk of human errors.
Pricing: ReguTech Solutions provides transparent pricing for ComplianceGuard, with plans starting at $139 per month.
Customer Reviews: Users commend ComplianceGuard for its up-to-date regulatory information and user-friendly document management system. The tool’s training modules receive positive feedback for enhancing overall compliance awareness.
In conclusion, these top 5 DPDP tools for 2024 cater to businesses seeking effective solutions to navigate the intricacies of data protection regulations. Each tool brings unique features and strengths to the table, empowering organizations to not only comply with the DPDP Act but also enhance their overall data security posture.
]]>What is Data Loss Prevention (DLP)?
Data Loss Prevention, often referred to as Data Leak Prevention, is a proactive approach to safeguarding sensitive information from unauthorized access, sharing, or loss. It involves a set of strategies, policies, and technologies designed to ensure that confidential data remains secure throughout its lifecycle.
Why is Data Loss Prevention Needed?
The increasing digitization of business operations has elevated the risk of data breaches. DLP becomes imperative to protect intellectual property, customer information, and other confidential data from falling into the wrong hands. The consequences of data loss can range from financial losses to reputational damage, making robust prevention measures a business necessity.
How is DLP Achieved?
DLP is achieved through a combination of policies, processes, and technological solutions. Robust access controls, encryption, monitoring, and employee training are integral components of an effective DLP strategy. Automated tools play a crucial role in identifying, classifying, and protecting sensitive data across networks, devices, and applications.
Market Trends and Growth
The market for DLP tools has witnessed substantial growth in recent years. With the increasing frequency and sophistication of cyber threats, businesses are investing more in DLP solutions to fortify their cybersecurity posture. The global DLP market is expected to continue its upward trajectory, driven by the rising awareness of data security concerns.
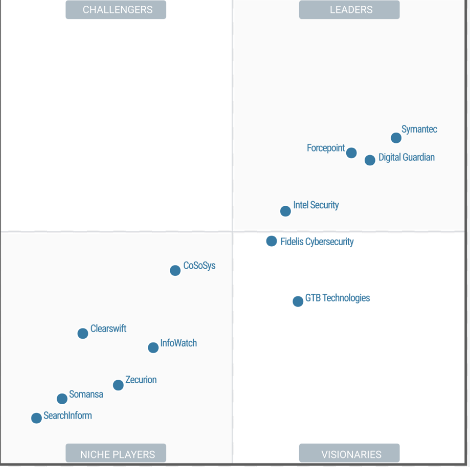
Market Segmentation
The DLP market is segmented based on deployment models, organization size, verticals, and regions. Cloud-based DLP solutions are gaining popularity due to their scalability and flexibility. Small and medium-sized enterprises (SMEs) are recognizing the importance of DLP, contributing to the growth of the market across various industries.
User Expectations
Organizations implementing DLP solutions expect comprehensive protection against data breaches, ensuring compliance with regulatory requirements. The use of advanced analytics and machine learning in DLP tools enhances threat detection and response capabilities, aligning with the evolving landscape of cybersecurity threats.
Industry and Market State for DLP Solutions
Industries such as finance, healthcare, and technology are at the forefront of adopting DLP solutions. The growing awareness of compliance regulations and the need to protect sensitive customer information are driving the demand for robust data protection measures. The market state reflects a dynamic landscape with constant innovations in DLP technologies.
Top 5 Data Loss Prevention Tools – Best Data Leakage Prevention Software
Symantec Data Loss Prevention Solution
Symantec, a leading cybersecurity provider, offers a comprehensive DLP solution that combines advanced threat intelligence with robust data protection features.
- Features: Symantec’s DLP solution excels in content discovery, policy enforcement, and incident response. It provides organizations with granular control over data access and movement.
- Pros: Users appreciate the user-friendly interface, making it accessible for both IT administrators and end-users. The tool’s customizable policies cater to the specific needs of diverse organizational structures.
- Cons: Symantec’s DLP solution can be resource-intensive, requiring organizations to allocate dedicated hardware resources for optimal performance.
- Customer Review: Users commend the tool’s accuracy in identifying and preventing data leaks, contributing to a positive overall experience.
- Pricing: Symantec offers tiered pricing based on organizational size and the specific features required, allowing businesses to tailor their DLP solution to their unique needs.
McAfee Total Protection for Data Leakage Prevention
McAfee is a prominent player in the cybersecurity arena, providing a holistic DLP solution that emphasizes real-time threat detection and response.
- Features: McAfee’s DLP solution boasts endpoint protection, encryption, and cloud-based DLP capabilities. The tool’s multi-layered threat defense ensures a proactive approach to data security.
- Pros: Users benefit from centralized management, scalability, and a comprehensive set of features that address various aspects of data protection.
- Cons: Some users find the initial setup to be complex, requiring careful configuration to ensure optimal performance.
- Customer Review: The tool receives praise for its proactive threat prevention capabilities and responsive customer support, contributing to a positive user experience.
- Pricing: McAfee offers flexible pricing based on the scale of deployment and the specific features required by the organization.
Forcepoint Data Leakage Prevention Software
Forcepoint stands out by offering a human-centric DLP solution that incorporates behavior analytics for a more adaptive and context-aware approach to data protection.
- Features: Forcepoint’s DLP solution includes behavioral analytics, incident response automation, and seamless integration with cloud services. This ensures a dynamic response to evolving cybersecurity threats.
- Pros: Users appreciate the adaptive security features, insider threat detection capabilities, and real-time policy enforcement that contribute to a robust defense against data breaches.
- Cons: Some users may experience a learning curve, especially when exploring advanced features, necessitating additional training for optimal utilization.
- Customer Review: The tool is praised for its accuracy in identifying and preventing data exfiltration, enhancing the overall security posture of organizations.
- Pricing: Forcepoint provides customized pricing tailored to organizational requirements, allowing businesses to align their investment with their specific DLP needs.
Digital Guardian Data Loss Prevention
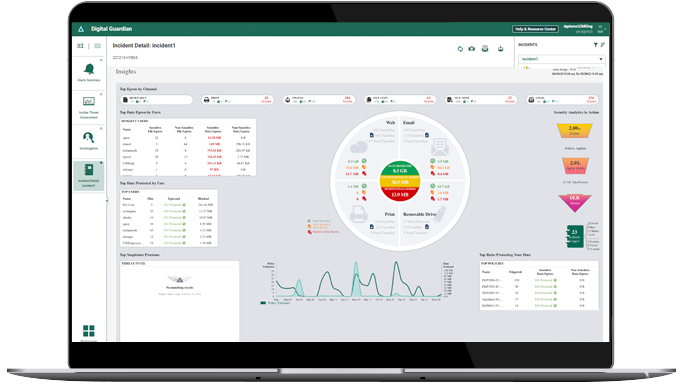
Digital Guardian specializes in providing endpoint-centric DLP solutions, focusing on ensuring the security of data at the point of use.
- Features: The tool offers endpoint protection, data discovery, and integration with threat intelligence sources. It provides organizations with granular control over data access and usage.
- Pros: Users benefit from the tool’s granular control features, robust reporting capabilities, and ease of integration with existing security infrastructure.
- Cons: Initial configuration complexity may be a challenge for some users, requiring careful setup and ongoing fine-tuning for optimal performance.
- Customer Review: Digital Guardian receives positive feedback for its effectiveness in protecting sensitive data, contributing to a strengthened security posture.
- Pricing: The pricing model is tailored, taking into account the scope of deployment and additional features selected by the organization.
Trend Micro DLP Software
Trend Micro’s DLP solution is known for its comprehensive features and cloud integration, addressing the evolving security needs of modern businesses.
- Features: The tool encompasses both endpoint and network DLP, encryption, and threat intelligence integration. It stands out for its seamless integration with cloud environments.
- Pros: Users appreciate the seamless integration with cloud services, real-time monitoring capabilities, and robust threat analytics that enhance overall data security.
- Cons: Some users may find the interface complex, particularly for beginners, necessitating a learning curve for efficient policy configuration.
- Customer Review: Positive feedback is received for its cloud-ready architecture and the tool’s ability to provide clear visibility into potential threats.
- Pricing: Trend Micro offers tiered pricing based on organizational size and the specific features chosen, allowing businesses to customize their DLP solution based on their unique requirements.
Top 5 Best Data Loss Prevention Software- Feature Comparison Matrix
| Features | Symantec DLP | McAfee Total Protection | Forcepoint DLP | Digital Guardian DLP | Trend Micro DLP |
|---|---|---|---|---|---|
| Content Discovery | |||||
| Policy Enforcement | |||||
| Incident Response | |||||
| Endpoint Protection | |||||
| Encryption | |||||
| Cloud Integration | |||||
| Behavioral Analytics | |||||
| Adaptive Security | |||||
| Insider Threat Detection | |||||
| Real-time Policy Enforcement | |||||
| Granular Control | |||||
| User-friendly Interface | |||||
| Customizable Policies | |||||
| Resource Intensiveness | (May require dedicated hardware) | (Complex initial setup) | |||
| Learning Curve | (Especially for advanced features) | (Especially for advanced features) | (Initial configuration complexity) |  (Interface complexity for beginners) (Interface complexity for beginners) | |
| Customer Reviews | Positive | Positive | Positive | Positive | Positive |
| Pricing Flexibility | Tiered pricing based on organizational size and features | Flexible pricing based on deployment scale and features | Customized pricing based on organizational requirements | Tailored pricing based on deployment scope and additional features | Tiered pricing based on organizational size and selected features |
Note: The features listed in the matrix are indicative and may vary based on specific product versions and updates. Organizations are encouraged to conduct a detailed evaluation based on their unique requirements and priorities.
Data Leakage Prevention is an essential component of modern cybersecurity strategies. As businesses navigate the digital landscape, investing in robust DLP tools becomes paramount. Understanding the market trends, segmentation, and top-performing tools enables organizations to make informed decisions in fortifying their data protection measures.
With the right combination of policies and advanced technologies, businesses can mitigate the risks associated with data breaches and ensure the security of their sensitive information.
]]>In this article, we will discuss what software deployment is, its advantages and potential challenges, finding the software deployment process that works for you, some best practices to follow and the top five software deployment tools in the market.
What is Software Deployment?
Software deployment is the process of rolling out an application, which could occur manually or automatically, throughout the IT environment. This deployment process can happen at the least intrusive times for an organization’s workforce, which could result in staggered releases to minimize interruptions to employee productivity and reduce strain on the system.
The tool that facilitates this process of app deployment is otherwise called Software Deployment Tool or Application Manager.
How does Software Deployment help Enterprises?
Software deployment plays a critical role in enterprise growth and security, especially when updates and patches are timely and consistent.
These updates and patches can help organizations meet their ever-changing business needs, and it differs from software release, which refers to the iterative process of any given application.
Software Deployment Advantages and Potential Challenges
Software deployments can meet the evolving needs of the business, improve security, add new features that address specific business needs, and enhance employee productivity by removing friction.
However, software deployments can also present potential challenges, such as undeployed patches due to a lack of available resources in the IT department. Streamlining approval workflows for software deployment can help mitigate these challenges.
Finding the Software Deployment Process that works for you
Each organization has different business needs, and every IT department within that organization has its own needs and challenges.
To find the software deployment workflow that best suits your specific requirements, you should consider setting up an ordered process for both stakeholders and IT teams, creating an ordered deployment checklist, looking for ways to optimize the process through automation, testing as much as possible to reduce bugs, and informing end-users of why an update is being pushed.
What are some other Software Deployment Best Practices to follow?
To ensure a smooth and secure rollout, here are some other best practices to consider for software deployment:
- Use continuous integration (CI) to ensure apps will work in your environment, not just in the dev’s personal sandbox.
- Adopt continuous delivery (CD) to prepare your code changes automatically to move from deployment to production through rigorous testing.
- Formulate a backup plan in case something goes wrong. Proactively plan for contingencies with a good rollback strategy in place.
Top 5 Best Software Deployment Tools – Choose Yours Now
Software deployment tools are essential for organizations that need to deploy and manage software applications across their IT infrastructure. These tools help automate the process, ensuring efficient and consistent deployments.
With so many software deployment tools available in the market, it can be challenging to choose the best one. In this article, we’ll review the top four software deployment tools and their features.
Microsoft Endpoint Configuration Manager
Microsoft Endpoint Configuration Manager (MECM) is a comprehensive software deployment tool that allows users to automate software deployments, updates, and patch management. It supports a wide range of operating systems, including Windows, Linux, and macOS, and can be used to deploy both traditional and modern applications.
Here are some key features of Microsoft Endpoint Configuration Manager (formerly known as SCCM) as a software deployment tool:
- Centralized management: Endpoint Configuration Manager provides a single console for managing all aspects of the deployment process, including software inventory, deployment, updates, and monitoring.
- Flexible deployment options: The tool supports a range of deployment scenarios, including client push, group policy-based deployment, task sequence-based deployment, and user-initiated deployments.
- Comprehensive reporting: Endpoint Configuration Manager provides extensive reporting capabilities, allowing administrators to track deployment success rates, compliance levels, and other key metrics.
- Patch management: The tool includes built-in patch management features, enabling administrators to automate the deployment of software updates and patches to keep systems up-to-date and secure.
- Integration with other Microsoft tools: Endpoint Configuration Manager integrates with other Microsoft products, such as Intune, to provide a more complete endpoint management solution.
ManageEngine Endpoint Central
ManageEngine Endpoint Central enhances software deployment with its Agent-Server Mechanism, fostering smooth communication and control. Automation facilitates swift and precise deployment across the network. The platform excels in Configuration Management, empowering sales reps to tailor settings as needed. Robust Management capabilities ensure oversight of deployment processes, while support for various platforms adds versatility.
Endpoint Central simplifies tasks with features like:
- Pre-defined Application Templates: Over 10,000 templates for instant package creation, saving time and ensuring accuracy.
- Self-Service Portal: Empowers users to install applications and patches independently, reducing help desk tickets.
- Pre and Post-Deployment Activities: Streamlines deployment by ensuring prerequisites are met and configurations are applied seamlessly.
- Software Repository: Central storage for reusable packages with options for Network Share and HTTP Repository.
- Installation/Uninstallation Using the Same Package: Simplifies the process for MSI, EXE, MSU, APPX, and MSP applications.
- Mobile App Distribution: Bulk deployment of apps with one click, supporting various formats.
- Scheduled Deployment: Optimizes resource usage by configuring deployment policies for off-hours.
- Enterprise App Catalogue: Simplifies app discovery, saving time and reducing the need for IT support.
- Install Applications as a User: Supports installing or uninstalling applications as a specific user, enhancing flexibility.
- Software Management Capabilities: Robust oversight of deployment processes for over 10,000 systems, rated 9 out of 10 for features.
Endpoint Central’s feature-rich design and user-friendly interface make it a powerful tool for efficient and automated software deployment.
Supported Platforms: Versatility in deployment across Windows, Mac, Linux, iOS, Android, tvOS, and chromeOS.
Ansible Software Deployment
Ansible is an open-source software deployment tool that allows users to automate software deployments and infrastructure management. It’s highly scalable and supports a wide range of operating systems, including Windows, Linux, and macOS. Ansible uses a simple syntax that makes it easy to learn and use.
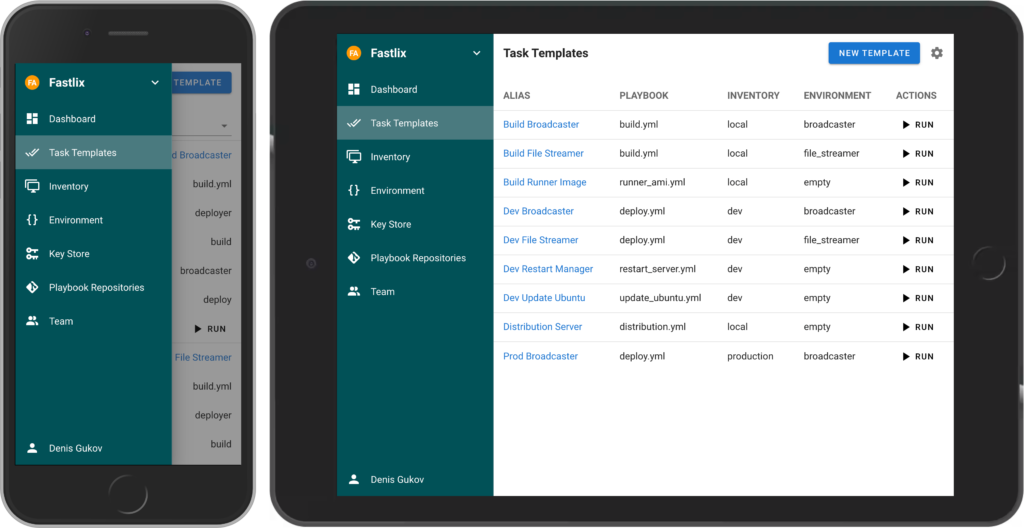
Here are some key features of Ansible as a software deployment tool:
- Automation: Ansible is an automation tool that allows for the deployment of applications, updates, and configurations to multiple servers at once, making it an ideal tool for large-scale deployments.
- Agentless: Ansible does not require agents or additional software to be installed on the target systems, making it easy to set up and use.
- Configuration management: Ansible can manage and automate configurations of entire infrastructures, allowing for a more efficient and streamlined deployment process.
- Playbooks: Ansible uses playbooks, which are a simple way to describe the deployment process and ensure consistency across different environments.
- Integration: Ansible integrates with a wide range of other tools and platforms, including cloud providers, containerization tools, and source control systems, allowing for a more seamless deployment process.
Puppet Software Deployment Tool
Puppet is a powerful software deployment tool that helps users automate the deployment and management of software applications across their IT infrastructure. It supports a wide range of operating systems, including Windows, Linux, and macOS, and can be used to deploy both traditional and modern applications.
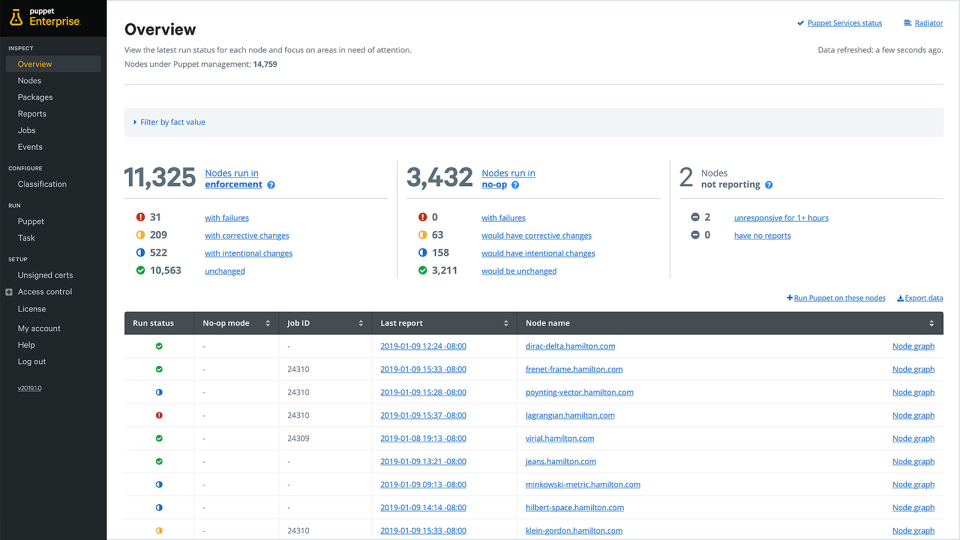
Here are some key features of Puppet as a software deployment tool:
- Infrastructure as code: Puppet allows you to define your infrastructure as code, enabling you to automate the management of your infrastructure.
- Cross-platform support: Puppet can manage a wide variety of operating systems and platforms, including Windows, Linux, Unix, and macOS.
- Scalability: Puppet is highly scalable and can manage large, complex infrastructures with ease.
- Reporting and auditing: Puppet provides detailed reporting and auditing capabilities, enabling you to track changes and monitor the health of your infrastructure.
- Extensibility: Puppet is highly extensible and can be easily customized to meet your specific needs.
- Agent-based architecture: Puppet uses an agent-based architecture, which means that it can manage infrastructure even if it’s not connected to the Puppet server.
- Version control: Puppet provides version control for your infrastructure code, allowing you to roll back to previous versions if necessary.
- Community support: Puppet has a large and active community, providing support and resources for users of all skill levels.
Chef Software Deployment Tool
Chef is a popular software deployment tool that allows users to automate the deployment and management of software applications across their IT infrastructure. It’s highly scalable and supports a wide range of operating systems, including Windows, Linux, and macOS. Chef uses a simple syntax that makes it easy to learn and use.
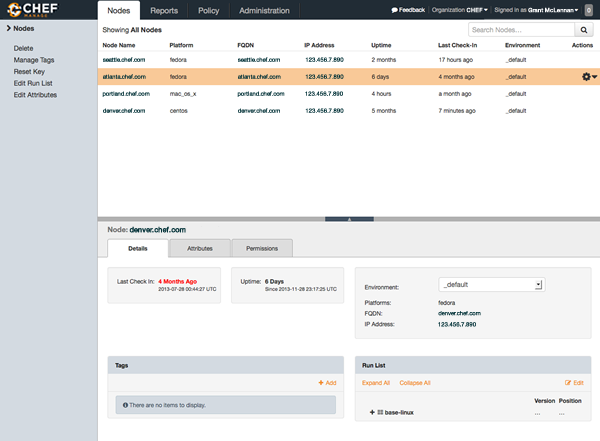
Here are some key features of Chef as a software deployment tool:
- Configuration Management: Chef is primarily used for configuration management, allowing users to automate the deployment of infrastructure and applications, as well as manage their state over time.
- Platform Support: Chef supports a wide range of platforms, including Windows, Linux, Unix, and macOS, allowing users to manage their entire infrastructure with a single tool.
- Idempotency: Chef uses an idempotent approach to configuration management, ensuring that resources are only changed when necessary and that the system remains desired.
- Integration: Chef integrates with a wide range of other tools and platforms, including cloud providers like AWS and Azure, as well as other configuration management tools like Ansible and Puppet.
- Community Support: Chef has a large and active community of users and contributors, providing a wealth of resources, documentation, and support to users of the tool.
Choosing the right software deployment tool can be challenging, but it’s essential for ensuring efficient and consistent software deployments across an organization’s IT infrastructure.
The four tools reviewed in this article, Microsoft Endpoint Configuration Manager, Ansible, Puppet, and Chef, are among the best software deployment tools in the market. Each tool has unique features and capabilities, and organizations should evaluate their specific needs to determine which tool is the best fit.
While it’s unlikely that any software deployment process will be completely free of issues, implementing best practices can help reduce potential risks. To achieve a smooth and secure rollout of software applications, it’s essential to have a clear understanding of what software deployment entails, the benefits it offers, and the challenges it may pose. By adopting recommended best practices, organizations can mitigate potential damage and ensure a successful deployment. Software deployment can often be bundled with device management tools like RMM, Endpoint Management and Patch management solutions.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, and Twitter.
You can reach out to us via Twitter/ Facebook or mail us at admin@thecybersecuritytimes.com for advertising requests.
]]>With hybrid work becoming a common thing, IT admins need an efficient way to manage those remote devices for several day-to-day operations.
Taking remote devices and managing a ticket will become hassle-free. In this article, we’ll see more about Remote Support Software and its importance for organizations.
What is Remote Support Software?
The process of managing a remote laptop, desktop, server or mobile device, to troubleshoot, file transfer, perform remote commands, modify registry settings, communicate with remote users, multi-monitor support, manage services and more is called Remote Support Software.
The need for remote support software is directly proportional to the variety and distribution of devices in your network.
If you have a robust remote monitoring and management (RMM) software then you may not need a remote support software to manage your devices.
Why will Remote Support Software ease things for IT admins?
IT admins need an efficient way to manage and control their remote devices to handle issues that are reported via help desk tickets, while certain tickets can be handled by a predefined automated configuration, the other tickets need technicians’ manual intervention to handle to issue instantly and remotely.
Issues like instant troubleshooting, remote chat and communication to understand the issue at the user end, remotely deploying commands, modifying registry, recording remote sessions, multi-monitor support for enhanced troubleshooting, remote managing of mobile devices via web app or mobile app for super-fast remote support management.
Top 5 Remote Support Software for 2024 – Remote Support Tools for IT teams and MSPs
The remote support software market has several providers and arriving at the best five remote support tools was challenging.
The below five tools were tested and analyzed from a primary point of research, while we also looked into the community of Internal IT teams and MSPs to get their feedback and see the tools that worked for them.
This list of remote support tools should be an ideal choice to begin your evaluation if you’re looking for a remote support system for your organization.
The Remote Support Software Grid – Best Remote Support Tools
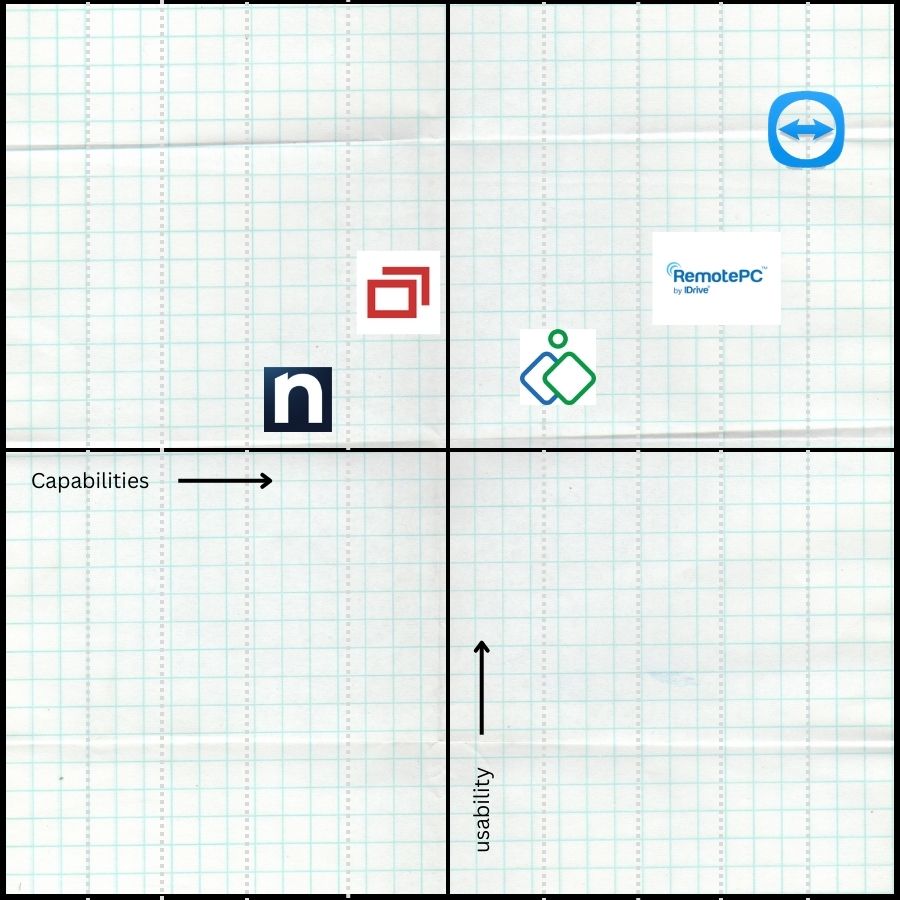
TeamViewer Remote Support Software
Teamviewer has done an amazing job with the quality and efficiency required for a remote support system.
The success behind the tool is the ease of use allowing even a layman to perform remote support operations compared to other tools in the remote support category.
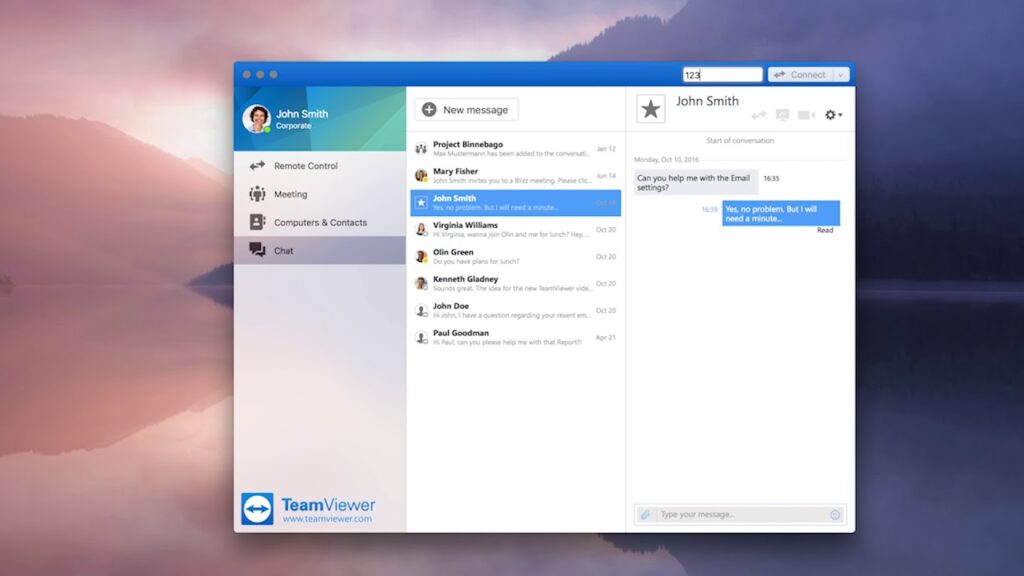
TeamViewer comes with remote troubleshooting, unattended access for elevated privileges, supports Windows, Mac, Linux, iOS and Android devices, file transfer, remote chat, multiple displays, meetings and remote video, thus competing with the space occupied by Zoom.
You can control any device using TeamViewer Remote Support Software.
Pricing: $123.90 per month for Teams, $240.90 for enterprise and $45.90 for Business (CAD)
ConnectWise Control Remote Support Software
ConnectWise Control’s Remote Support Software comes with flexibility, customization and world-class security for the managed devices.
It also provides custom configurations, granular control and user management, and live stream sessions for interactive communication between the user and technician. Supports hundreds of integration including Solarwinds, Zendesk, Freshdesk, Acronis, and more.
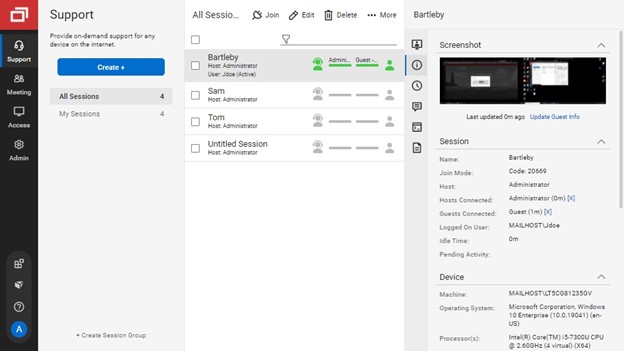
Covers a wide range of industry, technician-based roles, and product capabilities, and can fit into any type of organization network thanks to its enhanced remote support capabilities.
This remote support tool is a preferred option among MSPs and Small IT teams for the wide range of integrations and customizability it brings in.
Pricing: $42 per month for standard and $52 for premium.
Zoho Assist Remote Support Software
Zoho Assist has been one of the community favourites for SMBs and Startups thanks to its price, capability and ease of setting up.
With extensive remote support capabilities like remote troubleshooting, multi-monitors, session recording, video chat, text chat and remote calls, unattended access, file transfer, services and registry handling and more.
Zoho Assist has been the community favourite of MSPs and Small internal IT teams for its flexibility and ability to be integrated with its in-house and external third-party products.
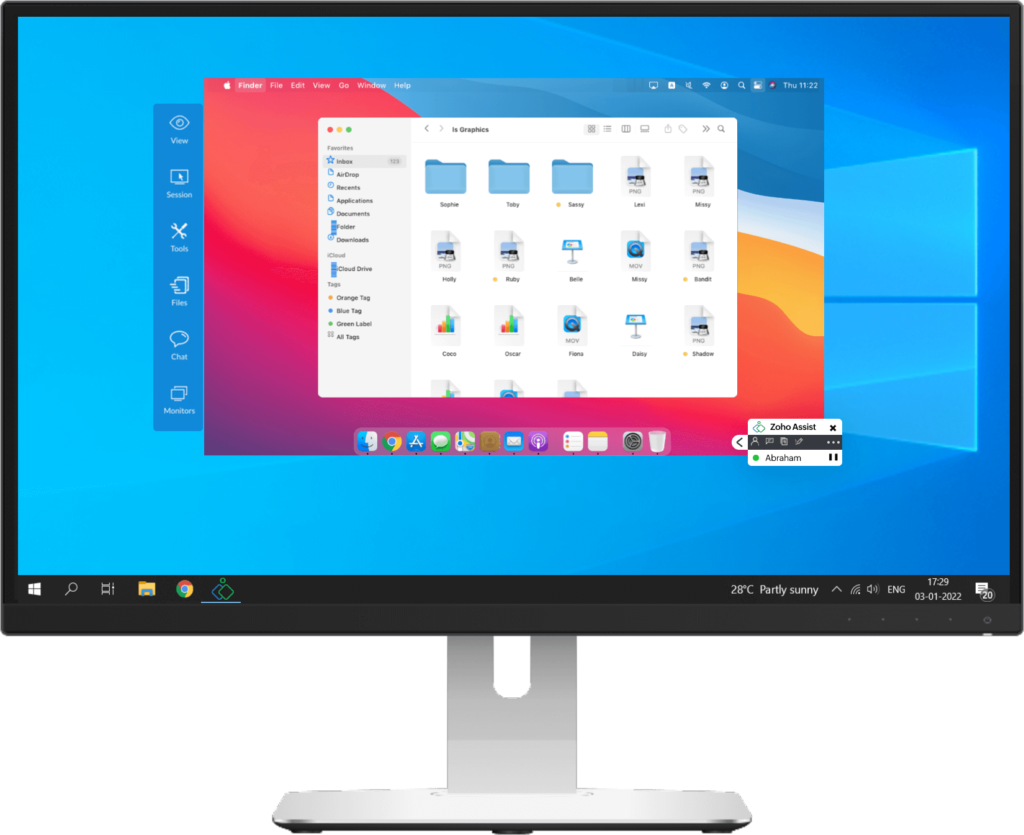
Also, it has been a leader in the Remote Support Software category in the G2 grid for a long time along with Teamviewer, ConnectWise Control and others.
Pricing: $13 per month for standard, $19 for professional and $30 for enterprise. Unattended also comes with similar rates.
RemotePC – Remote Support Tool
RemotePC comes with a decent amount of remote support capabilities including attended and unattended access, file transfer, always-on remote support, reboot, printing, multi-monitor, performance indicator, record sessions, endpoint backup, remote sound controls, logs, reports and more.
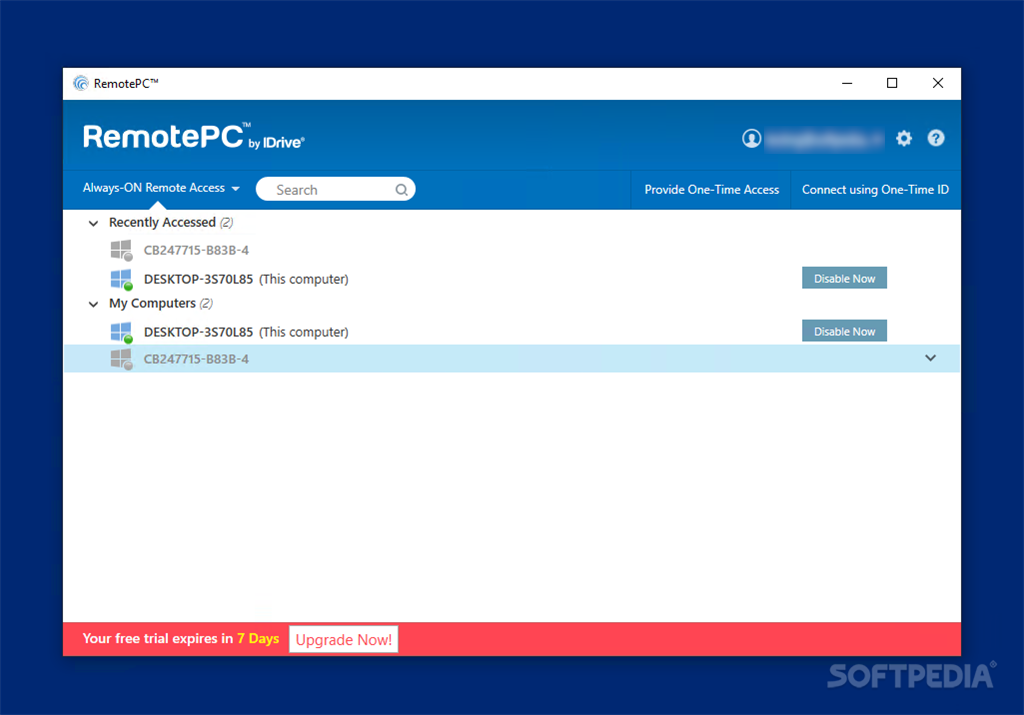
While RemotePC offers a wide range of features, sometimes the prospects may feel the capabilities are overwhelming for their requirement, other than that for businesses looking for a holistic and robust remote support software, RemotePC is a must-try.
Pricing: 29.95 per month for Teams, $59.95 for Enterprise, and $ 7.95 for SOHO.
Ninja One Remote Support Software
Although we are aware that Ninja One is an RMM and will fall mostly into that category, we wanted to place Ninja One in this listing only because of the community love and capabilities offered by this RMM vendor.
Ninja has an amazing RMM product which is supported by a decent remote support tool, it supports Windows, Mac and Linux all under one click.
The usability, remote support and access capabilities, user feedback and community’s favourite are the key reasons for NinjaOne to be part of the Remote Support Software category.
Apart from the remote support system, the tool also facilitates patching, app deployment, monitoring, helpdesk integration and more.
Pricing: US$3.00 per month per endpoint (source: Capterra)
Give a try on all these remote support tools and see which suits your network/budget perfectly. We would also honour Devolutions Remote Desktop Manager and GotoResolve for the product capabilities and for competing with a challenging remote support software category this year.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, and Twitter.
You can reach out to us via Twitter/ Facebook or mail us at admin@thecybersecuritytimes.com for advertising requests.
]]>What is ManageEngine Vulnerability Manager Plus?
ManageEngine Vulnerability Manager Plus is a multi-OS vulnerability management and compliance solution designed to provide end-to-end coverage, continual visibility, rigorous assessment, and integral remediation of threats and vulnerabilities.
It serves as a centralized console, making it an indispensable tool for empowering distributed workforces with secure working conditions.
Why Business should employ ManageEngine Vulnerability Manager Plus?
- 360-Degree Visibility: Gain insights into vulnerabilities, security misconfigurations, high-risk software, and web server misconfigurations across local and remote endpoints.
- Attacker-Based Analytics: Leverage analytics to prioritize areas more likely to be exploited by attackers, ensuring a focused and efficient vulnerability management approach.
- Platform Support: With support for Windows, Linux, and macOS (patch management only), Vulnerability Manager Plus is a versatile solution for various operating systems.
Vulnerability Manager Plus Architecture Overview:
At Zoho Corp. Site, an External Crawler continuously probes the internet, gathering crucial vulnerability information. This includes CVE ID, CVSS scores, severity details, exploit code, and patches. The Central Database, hosted on the Zoho Corp. site, acts as a repository constantly updated with the latest details on known and emerging vulnerabilities, patches, security configurations, web server hardening content, high-risk software lists, and compliance policies.
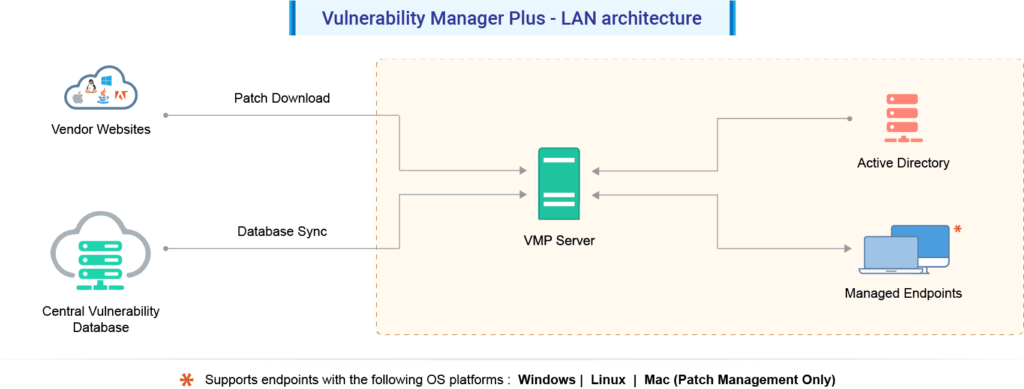
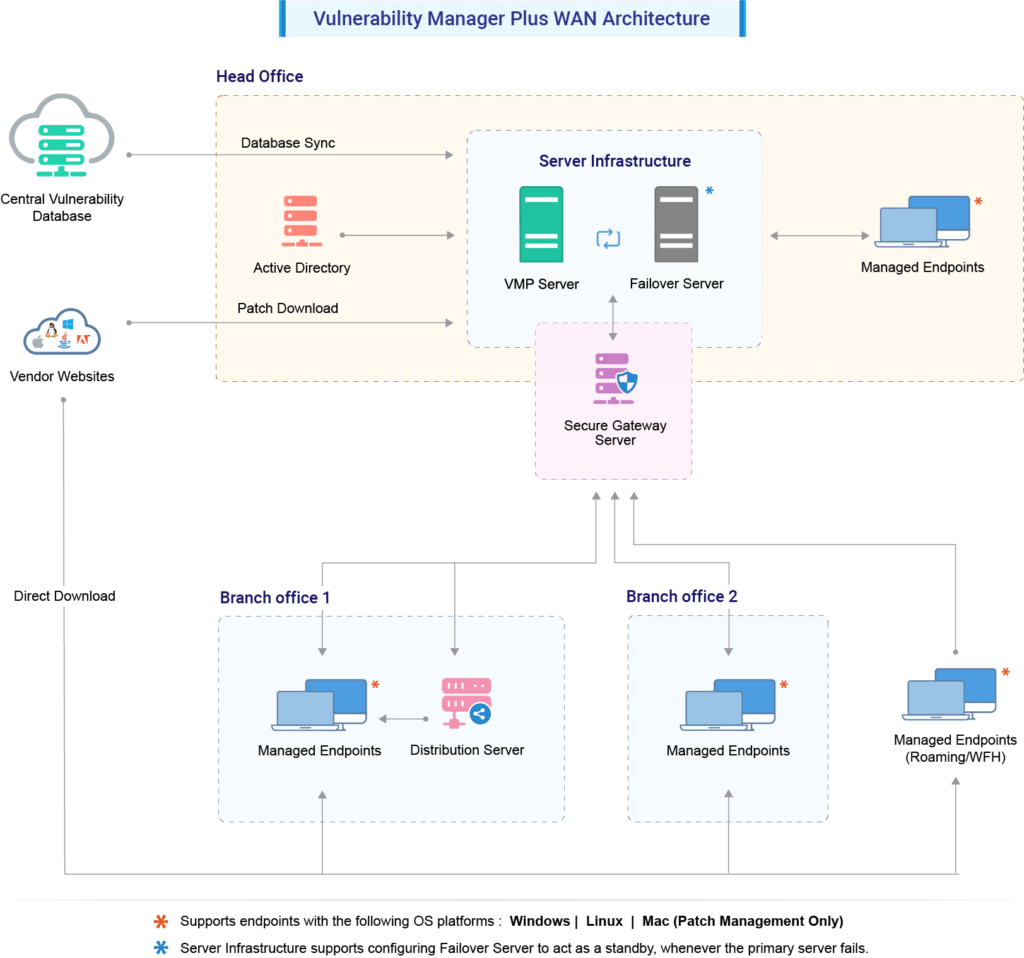
At the customer site, the Vulnerability Manager Plus Server, along with lightweight agents and a user-friendly web console, forms the core components. The server, subscribing to the Central Vulnerability Database, orchestrates tasks such as installing agents, scanning for vulnerabilities, deploying patches, and maintaining continuous communication, ensuring effective vulnerability management across the enterprise.
Features & Capabilities
- Vulnerability Assessment: Identify real risks based on exploitability, severity, age, affected system count, and fix availability.
- Compliance: Audit and maintain systems in line with 75+ CIS benchmarks, instantly identifying violations and offering detailed remediation insights.
- Automated Patch Management: Customize, orchestrate, and automate the patching process for Windows, Mac, Linux, and over 850 third-party applications.
- Vulnerability management for network devices: Strengthens network device security by creating a centralized inventory, executing scans for firmware vulnerabilities, and applying the latest patches to fix vulnerabilities.
- Security Configuration Management: Optimize system security by enforcing complex passwords, least privileges, and compliance with CIS and STIG security guidelines.
- Web Server Hardening: Obtain details on web server security flaws, helping establish and maintain secure servers resistant to various attack variants.
- High-Risk Software Audit: Identify and uninstall unauthorized and unsupported software, enhancing endpoint security.
- Zero-Day Vulnerability Mitigation: Deploy pre-built, tested scripts promptly to secure the network from zero-day vulnerabilities without waiting for patches.
Platform Support
- Windows: Vulnerability management software for Windows.
- Linux: Vulnerability management software for Linux.
- Mac: Limited to patch management for macOS.
For a detailed understanding of the Platform support, please take a look at the OS comparison matrix.
Pricing
ManageEngine Vulnerability Manager Plus is available in three editions:
- Free Edition: Suitable for SMBs, fully functional, managing up to 25 endpoints free forever.
- Professional: Suitable for computers in LAN, offering vulnerability scanning, system misconfiguration detection, and more – Starts at $695 for 100 Workstations and Single User License Annually.
- Enterprise: Suitable for computers in WAN, including all Professional Edition features, with additional capabilities like secure configuration deployment, compliance, automated patch deployment, and more – Starts at $1195 for 100 Workstations and Single User License Annually.
For a detailed comparison of the editions, please check the Edition Comparison Matrix.
Future of Vulnerability Manager Plus
In the ever-evolving landscape of cyber threats, adapting vulnerability management tools is paramount. ManageEngine stands at the forefront of this evolution, poised to meet the challenges of the future head-on. With a commitment to staying ahead of emerging threats, ManageEngine Vulnerability Manager Plus ensures the resilience of organizations in the face of dynamic cyber risks.
The foundation of ManageEngine’s future-proof approach lies in its provision of insightful reports that offer a comprehensive understanding of an organization’s security posture. By arming businesses with detailed and actionable insights, ManageEngine enables informed decision-making to fortify defenses effectively.
Moreover, ManageEngine’s proactive security measures set it apart in the fight against evolving threats. Through continuous updates and enhancements, the platform anticipates and addresses vulnerabilities before they can be exploited, fostering a proactive rather than reactive cybersecurity stance.
In conclusion, ManageEngine’s commitment to providing insightful reports and implementing proactive security measures positions Vulnerability Manager Plus as a robust solution ready to navigate the intricate landscape of future cyber threats successfully.
Final Verdict on ManageEngine Vulnerability Manager Plus
ManageEngine Vulnerability Manager Plus is an essential tool for businesses serious about maintaining a secure digital environment. With its comprehensive features, multi-OS support, and user-friendly interface, it stands out as a reliable solution in the vulnerability management space.
In conclusion, businesses looking to fortify their cybersecurity posture should consider ManageEngine Vulnerability Manager Plus for its robust capabilities and proven track record.
]]>MSPs and IT teams have started moving away from SCCM to other device management tools. In this article, we’ll see some of the best SCCM alternatives that you can look into while evaluating device management software like RMM, and unified endpoint management tools for your network and business.
Why IT admins are looking for the best SCCM alternatives?
Microsoft phased out SCCM as it has integrated its Intune and the all-new Endpoint Manager to suit the evolving market space.
However, not everyone was able to have a smooth transition into this new approach of Microsoft creating a lot of challenges for SCCM users, which is exactly why the existing users are looking for the best SCCM alternatives.
To know more about SCCM and Endpoint Manager in detail, please feel free to read our exclusive guide.
Finding the best SCCM alternatives is unique to each business
While SCCM has a wide range of scope, the best SCCM alternatives may not have all of it. However, they can actually fit into your network requirements and can be completely narrowed down as per your needs from the list of several device management tools on the market.
With the evolution of MDM, EMM and UEM, enterprises need to manage different types of devices including BYOD, Kiosk COPE, CYOD, COBO and COSU devices. They also need to have control over different OSs like Windows, Mac, Linux distros, ChromeOS, TvOS, FireOS, Android, and iOS.
The Top 4 best SCCM alternatives for your network
VMware Workspace One – First best SCCM alternative
VMware has been keenly following the footsteps of Microsoft and in some sections, they have better the Microsoft. This includes versatility, support and development.
VMware positioned itself as the leading unified endpoint management provider with abilities that Microsoft isn’t currently capable of doing. With the focus on Zero Trust, Digital Employee Experience and reduced digital friction VMware leads the efficiency and usability compared to SCCM, making it the best SCCM alternative.

Here is why VMWare is the best SCCM alternative.
- VMware comes with device management, remote support, remote access, analytics, virtualization, endpoint security and single sign-on.
- SaaS management capabilities.
- Predefined templates, configurations, and wizards reduced the IT admin’s time and increased efficiency.
- Enables actions on devices based on alerts and data.
- Intelligence reporting and insights facilitate rule-based automation.
- Enhanced patching capabilities
- Excellent documentation and support.
People who have used SCCM should find VMware more simple and straight-forward thanks to the user-friendly UX and UI of the platform. MSPs and IT admins looking for a solid MDM like capabilities with extended SCCM look alike perks, then they should go for VMware Workspace One.
Ivanti – Second best SCCM alternative
Ivanti follows VMware to be the next best SCCM alternative for IT teams and MSPs. Ivanti has intelligence and automation to provide, discover, self-healing, patching, zero-trust security and digital employee experience.
Ivanti has deep integrations with RiskSense, Cherwell Software, Pulse Secure and MobileIron making it a SCCM best alternative.
Here is why Ivanti is the best SCCM alternative.
- Supports Linux distros, Server OS, Android Open Source Project devices, OEM Config, and Wearables.
- Ivanti comes with machine learning, collects data and creates actionable insights used for the remediation of anomalies.
- Doesn’t just depend on CVE or CVSS but provides a contextual assessment of risk.
- Supports Linux distros, Server OS, Android Open Source Project devices, OEM Config, and Wearables.
- Supports OS and third-party patching with ITAM & ITSM capabilities.
- Excellent documentation and support.
Ivanti with its enhanced patching capabilities makes it the hot choice for the best SCCM alternative. Businesses and IT admins looking for a solid patching tool with extended SCCM capabilities should go for Ivanti.
IBM MaaS360 – Third best SCCM alternative
IBM Maas360 tool with its Watson (AI) is an advanced device management and endpoint security software. Watson is the key difference between SCCM, Vmware and Ivanti that makes the third place compared to other device management vendors in the market.
With the support of Watson, everything is super-fast and productive with IBM, it also comes with digital employee experience, several integrations, OS and application patching to strengthen the overall device and IT management needs.
Here is why IBM MaaS360 is the best SCCM alternative.
- IBM Watson identifies configuration and security changes on managed devices.
- Predefined configuration for 500 apps which be deployed to devices.
- Cloud-based patching with robust update capabilities, third-party application patching and vulnerability assessment.
- Endpoint analytics and automation improve the overall digital employee experience (DEX).
- Excellent documentation and support.
Managing devices efficiently and securely requires simple device management software that can satisfy the network requirements and also facilitate hassle-free device management routines for IT teams and MSPs.
ManageEngine Endpoint Central – Fourth Best SCCM alternative
ManageEngine Endpoint Central stands out as a strong alternative to SCCM for efficient device management and endpoint security.
Unlike traditional solutions, ManageEngine Endpoint Central simplifies device management with its user-friendly interface and robust features. It offers seamless integration of endpoint security, making it a reliable choice for IT teams and MSPs seeking simplicity and effectiveness.

Here’s why ManageEngine Endpoint Central is a good SCCM alternative:
- Intuitive Interface: ManageEngine Endpoint Central provides a straightforward interface, ensuring that managing devices is a hassle-free experience. The simplicity of the platform enhances productivity for IT teams.
- Endpoint Security: With a focus on security, Endpoint Central offers advanced threat protection and vulnerability management. It ensures that devices are safeguarded against evolving cyber threats, contributing to a secure IT environment.
- Application Patching: The platform streamlines application patching, offering efficient deployment of updates. It simplifies the process, ensuring that devices are up-to-date with the latest software patches and improvements.
- Comprehensive Automation: ManageEngine Endpoint Central incorporates automation to streamline routine tasks. This automation not only saves time but also enhances overall efficiency in managing devices across the network.
- User Experience Enhancement: Endpoint Central prioritizes the digital employee experience (DEX) by providing tools for endpoint analytics. This focus on DEX ensures that end-users have a smooth and optimized experience while using their devices.
- Reliable Documentation and Support: ManageEngine Endpoint Central is backed by reliable documentation and support, ensuring that IT teams have access to the resources they need for effective implementation and issue resolution.
In summary, for organizations seeking a dependable alternative to SCCM, ManageEngine Endpoint Central emerges as a solution that combines simplicity, security, and efficiency in managing devices and ensuring endpoint protection.
The above-listed device management tools act as the best SCCM alternatives that can ensure enhanced and robust endpoint management for your network and business.
Give a try on all the three best SCCM alternatives and choose the one that best suits your network.
There are also other good SCCM alternatives like Hexnode, NinjaOne, and Connectwise Automate which may suit SMBS while the earlier three would suit enterprises.
Find your best SCCM alternative after understanding your network and business requirements.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, and Twitter. You can reach out to us via Twitter/ Facebook or mail us at admin@thecybersecuritytimes.com for advertising requests.
]]>In this article, we’ll be looking at the top eight network firewall software tools that an enterprise needs to consider before purchasing one.
What is Network Firewall Software?
A Network Firewall is a security device that keeps the enterprise network free from malicious or anonymous traffic. Both internet and intranet connections can be secured using this device. Technicians can define firewall policies through which only authenticated and trusted devices will be able to access the enterprise network, and is more like a security at the front line that validates communication between internal and external networks.
Network Firewall is a crucial filter for DDOS activities, worms, viruses, trojans and other malicious intents outside of the enterprise network. An efficiently configured firewall policy will not provide access to any external devices except the ones that have permission to access corporate data inside the network. However, firewalls are just the first line of defense and not permanent armour against cyberattacks. Network Firewalls are broadly classified into software and hardware firewalls.
While we can understand firewalls in a separate article, in this piece we’ll be covering the top eight network firewall software tools for your enterprise.
1. Palo Alto Networks
Palo Alto Networks firewall is the leading network firewall software in the market. It has been the most preferred firewall software in the market, and Gartner has received more client requests for this software. Also with the acquisition of Twistlock and PureSec, Palo Alto Networks has scaled up its security options. It is also offering security operations and cloud security solutions to the market. Its latest version 9.0, comes with a DNS security service.
After showing improvement in SSL decryption performance, Palo Alto Networks has strengthened its share of large-scale data centres. One key point to pick Palo Alto Networks is that they have been part of Gartner’s Magic Quadrant for Network Firewalls for eight consecutive years.
With advanced firewall capabilities, and improvements in cloud offerings Palo Alto should be an optimal choice for users if there aren’t any budget constraints. It is a little expensive and can be a challenge for small and medium-level businesses. Without the SD-WAN feature, it is through third-party vendors and they are yet to offer a SaaS model. Though the presales team did receive great appreciation, the technical support team has not received the same in recent times, which could be because of the growing customer base.
Give a try on Palo Alto Networks here: https://www.paloaltonetworks.com/network-security/next-generation-firewall
2. Fortinet
Fortinet is another major player in the network firewall software category and is replacing dedicated routers as an edge appliance with firewalls. Unlike Palo Alto Networks, Fortinet’s pricing appears to be affordable, which helps the customers shortlist Fortinet for their network demands. With support for different firewall models like Alibaba Cloud, AWS, Google, Azure, IBM Cloud, Oracle OCI IaaS platforms and more, Fortinet is the best in the market for its features and affordability.
Fortinet covers endpoints, network, SIEM, NAC, switches and wireless access points. FortiGate firewalls from Fortinet are the most popular product developed by the vendor. With excellent features like virtual security processors, centralized management, reporting, new SD-WAN ASIC, and integrations, FortiGate is an excellent pick for enterprises of all ranges. While everything falls perfectly for Fortinet, the licensing model is found to be a little complicated, along with not-so-supportive technical support, and management complications when new features are released.
Give a try on Fortigate firewall here: https://www.fortinet.com/products/next-generation-firewall.html
3. Cisco
Cisco is a major IT organization with an excellent network, infrastructure and security space dominance. Most of the Cisco firewalls do go along the large infrastructure deals won by Cisco. Existing Cisco customers are in the mindset to pick Cisco firewalls more than others. It sells multiple firewalls like Adaptive Security Appliance (ASA) 5500-X Series and ASAv, virtual firewall appliances, Meraki MX series, Cisco iOS firewall and more. Cisco’s Firepower Management Center (FMC) is an on-premise solution that can be managed centrally and made available for firepower and ASA 5500-X devices.
Cisco VPN client offers support for mobile devices, and the VPN tunnels are stable compared to others. Though the infrastructural giant has a lot of benefits, still clients are complaining about deploying firepower VMs on IaaS platforms and because of this Cisco is not deployed in the public cloud, unlike other vendors. FMC lacks maturity compared to other vendors, like no integration with endpoint detection and response tools (EDR) and network security policy management tools (NSPM). Excluding these two cons, Cisco is perfect for corporate network firewall management.
Give a try on Cisco Firewall Management: https://www.cisco.com/c/en/us/products/security/firewalls/index.html
4. ManageEngine Firewall Manager
ManageEngine’s Firewall Analyzer is a robust tool to streamline network security management. This solution empowers sales teams by providing insights into firewall and network activities, enhancing their ability to articulate the product’s value to potential customers. Its intuitive interface facilitates easy comprehension, ensuring sales reps can efficiently convey its benefits.
Key Features:
- IP Address & Switch Port Management
- Firewall Policy Management
- Bandwidth Analysis
- Change Management
- Fault Management
- Network Security Management
- Firewall Log Management
- User Internet Activity Monitoring
- Real-time VPN and Proxy Server Monitoring
- Network & Server Monitoring
- Compliance Management
- Network Forensic Audits
- Log Analysis
- Configuration Management
- Network Traffic and Bandwidth Monitoring
Pricing: 1 Device Pack with 2 Users starts at US $395 for Standard Edition.
5. Checkpoint software technologies
Checkpoint Software Technologies is one of the leading players in the network firewall software tools category. However, as per Gartner research, their influence in this category is reducing compared to other players. It has introduced four new security gateway appliances in the last year and also acquired Dome9 for cloud security posture management. It offers 23 security gateway models ranging from low to high-end options.
With a simple pricing model, and the next-generation firewall features Checkpoint Software Technologies is a wonderful pick for a business. Features like centralized management, multi-domain security management and smart provisioning for MSSPs make it the client’s favourite. However, technical support is the issue as level 3 escalations take longer than levels 1 and 2, with poor communication on the progress at the development end.
Give a try on Checkpoint Software Technologies firewall management here: https://www.checkpoint.com/products/next-generation-firewall/
6. Huawei
Huawei is China-based tech giant that is also involved in the network firewall software tools domain. It includes the Unified Security Gateway (USG), virtual series and Eudemon. Users who are already using Huawei products are most likely to use the firewalls too. It comes with mature SD-WAN capabilities for different scenarios. Huawei firewalls support TLS 1.3, offering deep SSL decryption and traffic inspection options for encrypted communications.
Along with the above options, Huawei offers integration with an SIEM solution, Cybersecurity Intelligence Systems (CIS) and has a simple integration procedure. However, the vendor appears to be lagging in cloud-based services, and the offerings are mostly appliance-targeted. Roaming users and distributed offices need to be taken care of as a SaaS offering.
Give a try on Huawei’s firewall management tool here: https://e.huawei.com/in/products/enterprise-networking/security/firewall-gateway/usg6600
7. Sophos
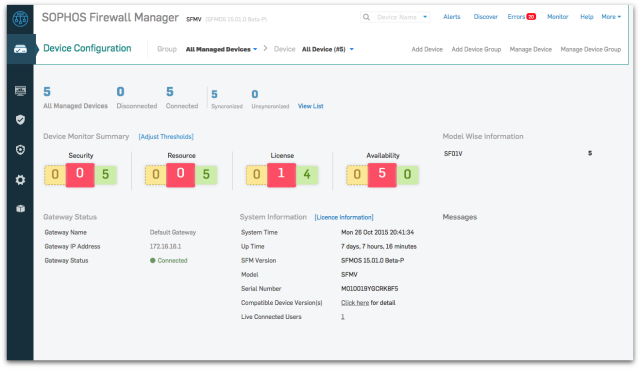
Sophos is a leading endpoint and network security vendor from the UK. It’s known for its unified threat management (UTM) market share and also offers robust network firewall software and endpoint security integrations. More applicable to SMBs than enterprises. With the new synchronized security system, chrome authentication, air gap support and central cloud management console for XG firewalls Sophos is delivering the right capabilities to its market segment. It comes with native TLS 1.3 decryption unlike other players, and offers multi-cloud visibility. Also, it owns strong real-time ransomware detection capabilities and coordinates with endpoint and firewalls for threat detection and endpoint health management.
However, Sophos lacks certifications such as EAL4 and also lacks integration with third-party EDR tools. And need to improve on the SaaS offerings like FWaaS, DL, and CASBs integration.
Give a try on Sophos firewall here:https://www.sophos.com/en-us/products/next-gen-firewall.aspx
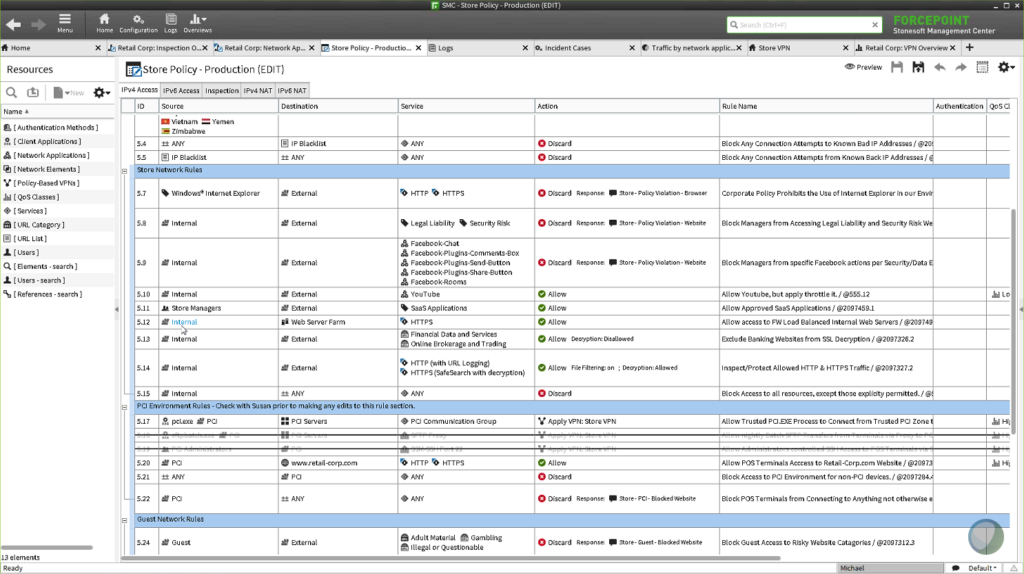
8. Forcepoint
Forcepoint is another security vendor based out of the United States in the space of network firewall software tools. It has a good potential in the market, it should be more responsive and improve the focus to expand customer base. SD-WAN has to be a little mature and management of virtual environments like AWS, VMware, and Azure is now made available. The Security Management Center (SMC) is intuitive and hassle-free for managing appliances, ISO images and software. Owns a mature IDPS offers, with threat intelligence from McAfee GTS, best clustering capabilities, and simple VPN configuration templates with a simple UI.
Furthermore, it owns user entity behaviour analytics (UEBA) capabilities, with advanced threat detection inclusive of sandboxing. On the contradictory, Forcepoint lacks EDR integration with third parties and is yet to provide a SaaS model to keep up with the market pace. Needs to introduce FWaaS, along with its existing multi-cloud support.
Give a try on the Forcepoint firewall offering here: https://www.forcepoint.com/product/ngfw-next-generation-firewall
All these firewall software tools help secure the enterprise by being the first line of defense but are not sufficient to combat cyberattacks. As an enterprise, a robust firewall is the first step for a secured network. Give a try on these network firewall software offerings and let us know which suits you.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, Instagram, and Twitter.
]]>When it comes to keeping track of a company’s assets, a variety of asset management apps are now available, which save time and improve efficiency.
In this article, we’ll go over everything there is to know about IT asset management tools.
What is IT asset management (ITAM)?
IT asset management, also known as ITAM, is the process of ensuring that an organization’s assets are properly identified, deployed, maintained, upgraded, and disposed of.
Simply put, it is the process of ensuring that your organization’s valuable assets, both tangible and intangible, are tracked and used. An IT asset is anything that a company values, such as hardware, software, or information.

Why is IT asset management important
IT asset management is crucial to a business’s success. It centralizes the company’s financial, inventory, and contractual functions to support strategic decisions about the use and distribution of IT-related materials among employees.
Here are a few examples of ITAM’s significance.
- The usefulness of IT assets is limited. The IT asset lifecycle can be proactively managed to maximize the value an organization can derive from it.
- Applying processes across all lifecycle stages to understand the total cost of ownership and optimize the use of assets is an important part of IT asset management.
- The asset management practice of a company goes far beyond the hardware that has received an official IT stamp of approval.
- New asset management challenges arise as a result of subscription-based software and employees’ expectations to customize the tools they use through marketplaces and app stores.
- Modern teamwork necessitates IT teams being adaptable and adapting their asset management process to best enable the business.
- Asset management has become an even more important part of an organization’s overall strategy because it provides up-to-date information that helps to reduce risks and costs.
- When it comes to budgeting, lifecycle management, and making decisions that affect the entire organization, an asset management process creates a single source of truth.
- Collaboration is also a crucial component of successful asset management. Instead of purchases being made in secret, a collaborative tool allows employees to make requests and other teams, such as procurement, to comment on and approve purchases.
How to effectively perform IT asset management
It’s difficult to track and manage all of your hardware, software, virtual, and non-IT assets from a single location without a well-thought-out strategy and a well-defined process flow. As a result, implementing an IT asset management (ITAM) system is a wise decision.
It also provides you with a plethora of advantages, some of which are:
- Find and enlist an executive sponsor who will champion ITAM in a visible and active manner.
- Carefully organize your ITAM implementation team. Bring them in early on and give them the opportunity to build the practice from the ground up.
- Select a manageable pilot, work on it, test it, and improve it before expanding it to other areas.
- Define the parameters by which a critical asset is defined. It’s possible that it’s a particular piece of hardware. It’s possible that it’s a specific piece of software. You’ll get a long list of assets from discovery tools.
- Don’t try to reinvent the wheel when it comes to ITAM; instead, use a lifecycle-based approach.
- It is entirely up to you whether or not to use a CMDB. Consider what data you’d like to feed the CMDB. While it can be a valuable single source of truth, it does not have to contain all of your data. Only include information that adds value.
- Your ITAM practice will benefit from automation. Introduce automation wherever possible. Look for new opportunities for automation on a regular basis, as technology in this area is rapidly evolving.
- The asset data can also help with change management, ensuring that changes do not result in unplanned outages or other issues that could affect critical services or business users.
- Make certain you have all of the necessary licensing documentation. Ascertain that your ITAM processes compare deployed instances to this data. This will ensure that there are no unpleasant surprises when the software auditor arrives.
- Allow for a feedback system to assist you in improving over time. Make preparations for process evolution and change. The more time you spend running ITAM and integrating it into your environment, the more you’ll learn.
Top 6 IT asset management tools – Best IT asset management software for 2024
Snipe-IT – IT asset management software
Snipe-IT is an online IT asset management software app that is open-source. The app comes with a slew of features that make inventory management a breeze. A summary of recent activity is displayed on the dashboard. The REST API can also be used to integrate the app with your own system.
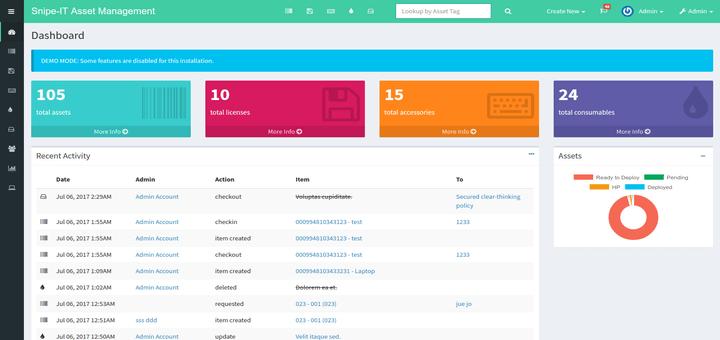
Features
- Web-based software
- Secured data
- One-click backups
- Per-user language support
- Multi-language translation
- Mobile-friendly for asset updates
- LDAP login/user sync
- JSON login/user Sync
- Slack notification integration for check-in/ checkout
Pricing: $39.99/months
Auvik – IT asset management tools
Auvik IT asset management tool can discover and distribute IT assets automatically. It provides visibility into every device’s connectivity as well as the network’s configuration. It has network visibility and IT asset management capabilities that can be automated.

Features
- Discovery & mapping
- Inventory & documentation
- Hardware lifecycle data
Pricing: Get quote plans, Essentials and performance.
ManageEngine Asset Explorer
Efficiently manage your IT assets with ManageEngine AssetExplorer, a user-friendly web-based IT Asset Management (ITAM) solution. This tool ensures a comprehensive approach from planning to disposal, offering seamless tracking of software and hardware assets, software license compliance, and purchase order management. Discover the benefits of unified agent asset discovery for Windows, Linux, and macOS assets, and make informed decisions throughout the IT lifecycle.
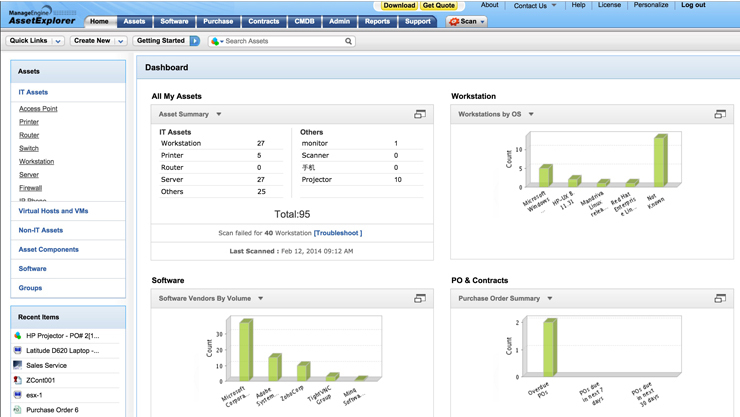
AssetExplorer simplifies IT asset inventory management, software license management, software asset management, purchase order management, asset life cycle management, asset tracking, and configuration management database.
Features:
- Unified agent for asset discovery across Windows, Linux, and macOS.
- Comprehensive software and hardware asset management.
- Software license compliance monitoring.
- Purchase order and contract tracking.
- Complete IT asset life cycle management.
- Precise asset tracking software.
- Configuration Management Database for efficient decision-making.
Pricing:
- Free Edition:
- Full functionality.
- No expiration.
- Limited to 25 nodes.
- Available in 29 languages.
- Trial Edition:
- Fully functional 30-day trial.
- Valid for 30 days.
- Limited to 250 nodes.
- 24×5 live technical support.
- Available in 29 languages.
- Professional Edition:
- Fully functional.
- Valid until the license expires.
- Manage nodes based on the purchased license.
- 24×5 live technical support.
- Available in 29 languages.
Choose the edition that suits your needs, and experience seamless IT asset management with AssetExplorer.
Asset Panda – IT asset management tools
Asset Panda IT asset management software can be used to manage both physical and digital assets. Creating workflows and actions will help you automate the asset management process.
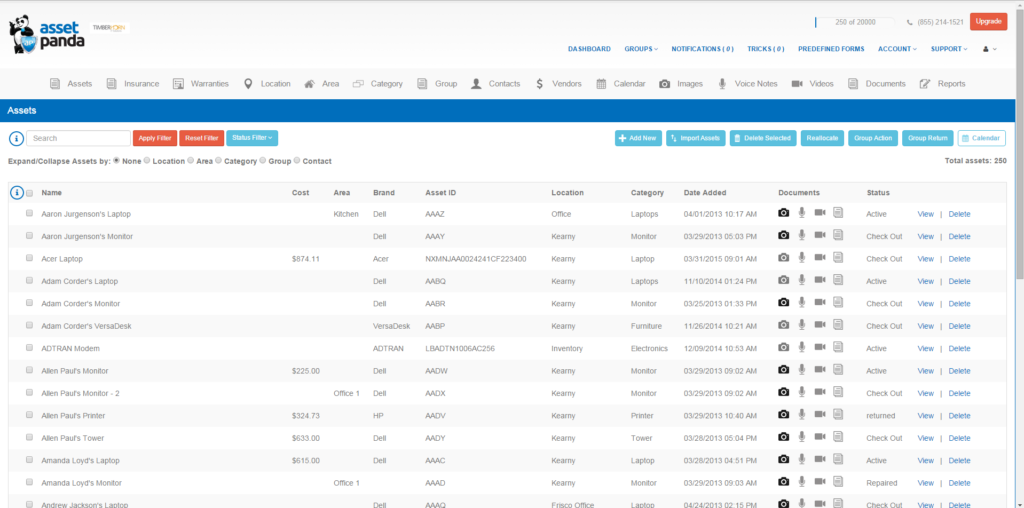
Features
- Asset Register- asset tracking
- Relationships- asset tracking
- Costs-asset tracking
- Location- asset tracking
- Status- Asset tracking
- History- asset tracking
Pricing: Asset panda’s pricing information is provided by the software provider or gleaned from publicly available pricing materials.
Spiceworks – IT asset management software
Spiceworks IT Asset Management software allows you to keep track of the hardware and software on your network. All types of network devices, such as switches, routers, gateways, and others, can be monitored. The software will detect assets on the network automatically, categorize them, and generate a detailed report.
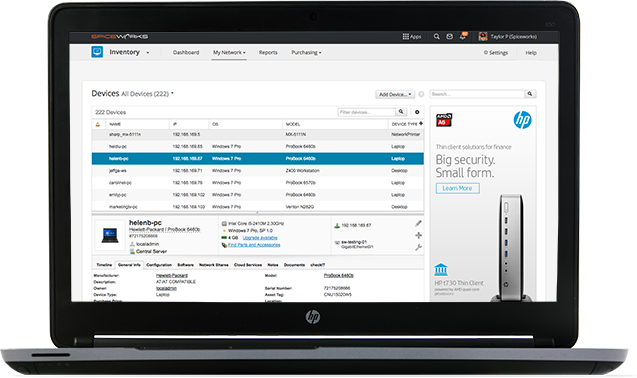
Features
- Monitor network licenses and devices
- Manage license
- Network
- Exchange
- Report on inventory
- Assets
- licensing.
Pricing: Free
Freshservice – IT asset management software
Freshservice is an online IT asset management tool that can assist you in keeping track of your hardware, software, contracts, and other assets. Assets can be categorized by location, creator, date of creation, and asset type. You can track assets as they progress through different stages and even get a quick timeline.
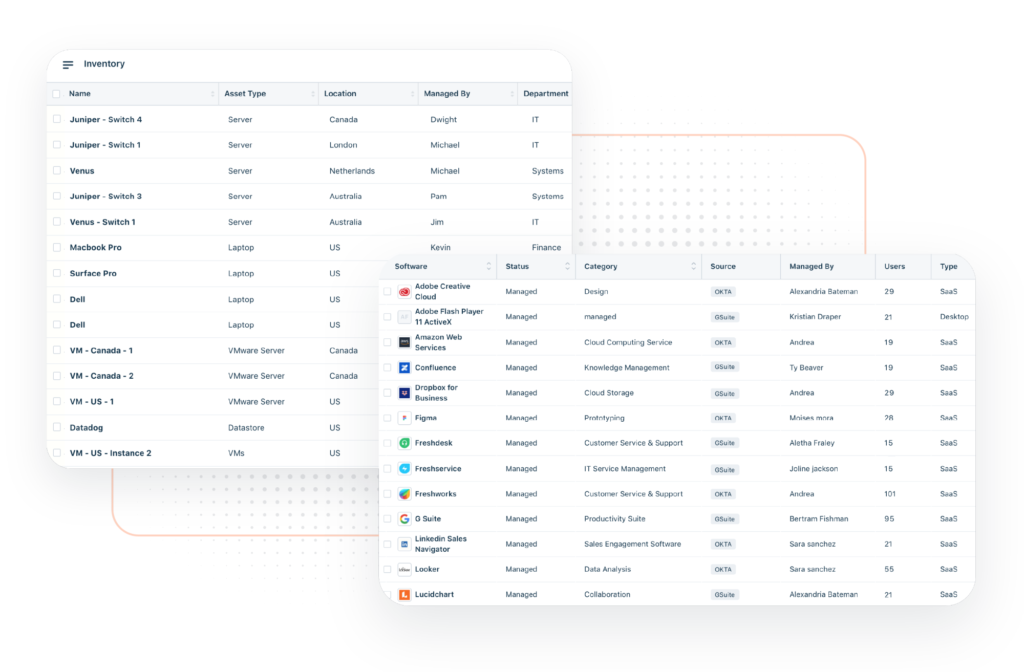
Features
- Asset management
- Custom & scheduled reports
- Incident management
- Multiple languages
- License management.
Pricing: $19 to $99 per user per month.
Honorable IT asset management tools – Asset Management Software
ManageEngine Asset Explorer – IT asset management software
ManageEngine Asset Explorer is a web-based IT asset management tool that aids in the monitoring and management of your network’s assets from planning to execution. Asset Explorer gives you a variety of options for discovering all of the assets in your network. You can track purchase orders and contracts, manage software and hardware assets, and ensure software license compliance.
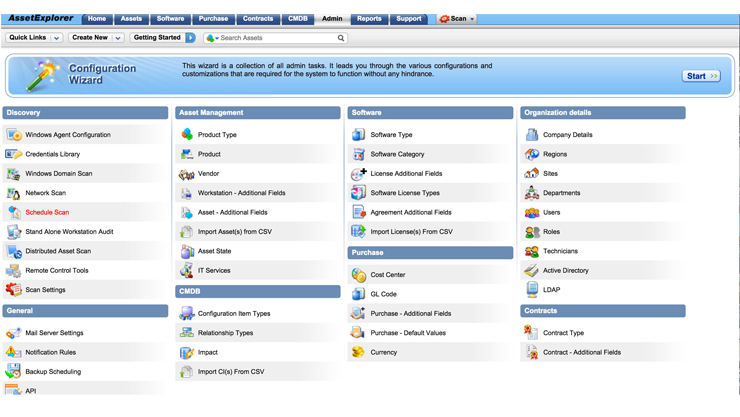
Features
- Asset Lifecycle Management
- Hardware Asset Management
- Software Asset Management
- Software License Management
- License Compliance Management
- CMDB
- Purchase orders and Contract Management
- Remote Control
- Reporting.
Pricing: Free Edition: Fully functional, restricted to 25 nodes. Professional bundle starts at $955/year for 250 IT assets annually.
Ninja One – IT asset management software
NinjaOne IT asset management software provides a risk-free trial of their software. Ninja is sold on a per-device basis, with prices varying depending on the features required. Managed service providers (MSPs) and IT professionals can benefit from NinjaOne’s powerful and intuitive server management software. Ninja includes tools for monitoring, managing, securing, and improving all of your network devices, including Windows servers, workstations, and laptops, as well as macOS devices.
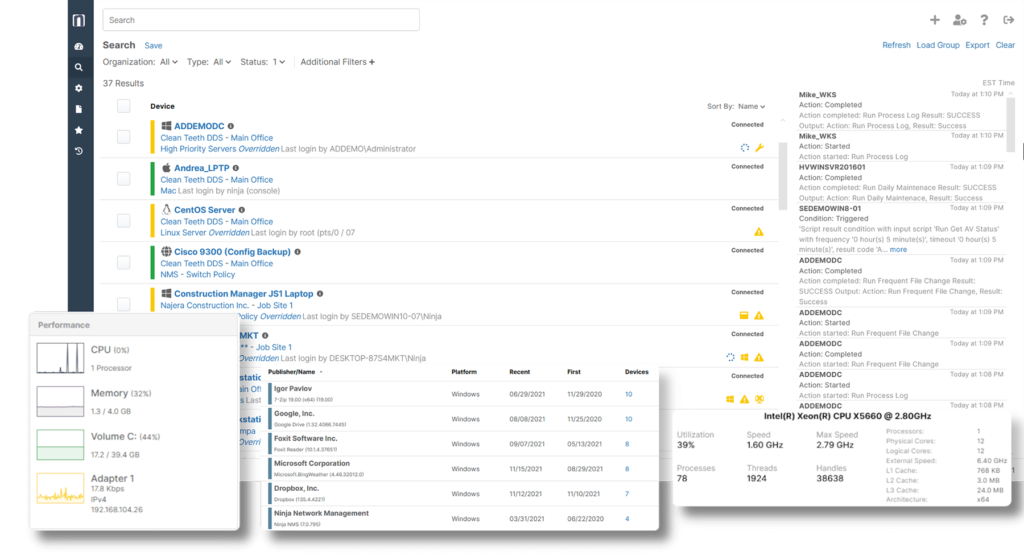
Features
- Recurring tasks
- Task dependencies
- Team chat
- Time tracking & reporting.
Pricing- Starter: $39 per month, Pro bundle starts at $79 per month, and Business bundle starts at $124 per month.
Nifty – IT asset management tools
Nifty is a collaboration hub that provides visual project management, allowing IT teams to see their workflows in real-time. nifty access to longer-term, schedule-driven implementations, as well as nimble workflows like ticket management that can be automated and measured after the fact. Nifty is the tool that your team will rally around, whether you’re looking to manage a process or speed up resolutions.

Features
- Time tracking
- Client invoicing
- Mobile time tracking
- Administration tools
- API/integration
- Task prioritization
- Project map
- Project budgeting
- Resource management
- Project monitoring
- Community forum
- Task ranking
- Workflow management
- Business instant messaging
- Platform basics
- Content planning
- Task creation
- Task management
- Project management
- Remote collaborations
- Marketing campaign performance.
Pricing: $39/month for up to 10 team members, Pro bundle starts at $79/month for up to 20 team members, Business bundle starts at $124/month for up to 50 team members, and Enterprise bundle starts at $399/month for unlimited team members
Trending IT asset management tools – ITAM software
Asset Cloud – IT asset management software
Asset Cloud is a multi-purpose IT asset management software application. You can use the app to manage both physical and digital assets. Pre-built reports can be generated to keep track of overdue checkouts, warranties, scheduled maintenance, and more.
Features
- Asset management
- Document management
- Fixed assets
- Collaboration
- Tax management
- Surveys and feedback
- Analytics
- Knowledge base
- Version control
- Incident management
- Task tracking
- Reporting
- Asset budgeting
- Asset lifecycle management
- Disposal management
- Asset sharing.
Pricing
Basic- $46/month
Plus- $75/month
Complete- $115/month
Go Codes – IT asset management software
GoCodes is a powerful IT asset management program. Custom fields, QR codes, audits, excel imports and exports, GPS tracking, maintenance, APIs, reports, analytics, and inventory management are all supported in the free version of the software. If you want advanced features like a company URL, data backups, recurring services, asset stock transfers, and advanced access control, you can upgrade to the paid version.
Features
- Audit trail
- document management
- Inventory management
- Reminders
- Work order management, inventory tracking
- Supplier management, status tracking
- Tax management
- Barcoding/RFID
- Historical reporting
- To-do list
- Audit management
- Inspection management
- Vehicle tracking
- Purchasing
- Alerts/notification
- Service history.
Pricing
Standard – $459/annually
Premium- $810/annually
Premium elite- $1,500/annually
Professional – $2,160/annually
Invgate Insights- IT asset management software
InvGate Insights is an amazing asset management software. The software enables the discovery and management of IT assets. By compiling asset information from network discovery data and third-party sources, you can create a single repository of assets.
Features
- Network discovery
- Asset inventory
- IT financials
- Software licensing
- Software metering, asset monitoring
- Software deployment
- Remote desktop
- Integration with service desk
Pricing- Free trial, quotation-based.
Ivanti – IT asset management software
Ivanti is a IT asset management software system that allows you to inventory and manage your computers remotely. It can generate reports on installed software and hardware, provide remote support, and apply security patches.
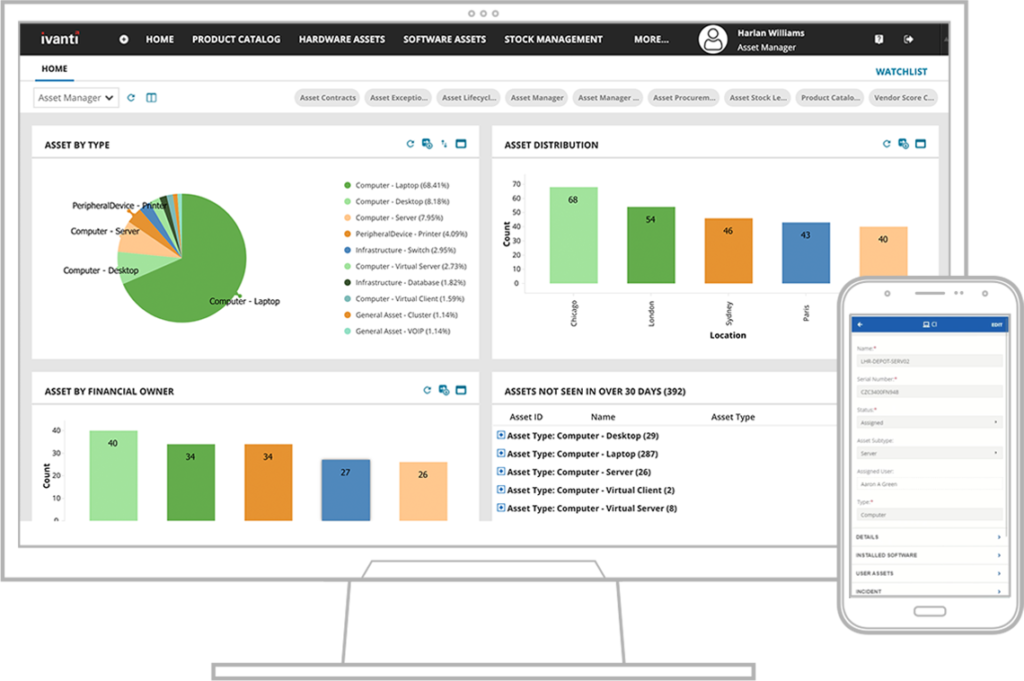
Features
- Asset management
- Document management
- Self-service portal
- Collaboration
- Inventory tracking
- Analytics
- Knowledge base
- Version control
- Alerts/escalation
- Incident management
- Task tracking
- Reporting
- Asset tracking
- Asset sharing
- Keyword search
Pricing- $50/annually
SolarWinds – IT asset management software
SolarWinds Service Desk includes a fully integrated IT asset management software suite that combines powerful tools and capabilities into a single, web-based platform. Computers, servers, laptops, mobile devices, networking equipment, and virtually any other technology asset can be tracked as part of your organization’s hardware and software inventory.
Features
- Asset centralization
- Finding assets for Windows and importing assets from other repositories
- Maintaining inventory and keeping records
- Troubleshooting via integration with Dameware Remote Support software
- You can use this reporting engine to create pre-configured and custom reports.
Pricing
Business- $19/month
Professional- $39/month
Enterprise- $89/month
Conclusion
IT Asset management is adapting as IT continues to evolve, with more reliance on SaaS vendors for critical services, and it’s necessary to track changes in increasingly dynamic cloud environments. It’s critical that you select the tools that will allow you to collaborate effectively and support your service management practice.
Each organization is distinct from the others. It’s possible that you’ll have to map out complex dependencies across an organization. To reduce risk, intangible assets such as licenses and compliance documents should be tracked. Perhaps your needs are more straightforward, such as keeping track of a computer inventory.
Choose software that meets your company’s needs after careful consideration and thorough research. Before you buy any software, make sure to read the online reviews and ratings.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, Twitter, and Reddit.
You can reach out to us via Twitter/ Facebook or mail us at admin@thecybersecuritytimes.com for advertising requests.
]]>This review will delve into the software’s key aspects, including its purpose, features, platform support, pricing, industry recognition, and customer testimonials.
What is ManageEngine Endpoint Central?
Endpoint Central is an all-encompassing UEM solution that addresses the need for unified management of devices, applications, and data. It offers automated patching, asset intelligence, remote troubleshooting, data security, attack surface management, and ransomware protection, all from a single console. This tool empowers IT teams to manage their digital workplaces efficiently.
Why Businesses Need ManageEngine Endpoint Central?
In the modern IT landscape, managing diverse endpoints, including laptops, mobiles, desktops, and servers, is crucial for business operations. ManageEngine Endpoint Central aims to bring everything in IT together, providing visibility and control over the entire infrastructure.
The software is positioned as a solution to enhance security, user experience, and overall business agility while ensuring compliance with industry standards.
Endpoint Central Features & Capabilities:
Endpoint Central offers a plethora of features and capabilities, making it a robust UEM solution:
- Automated Patching: Secure networks by automating patch deployment for various operating systems and third-party applications
- Ransomware Protection: Gain insights into the root cause of ransomware attacks, provide immediate incident response, and prevent future attacks.
- Threat Detection and Remediation: Constantly monitor and remediate vulnerabilities based on 75+ CIS benchmarks.
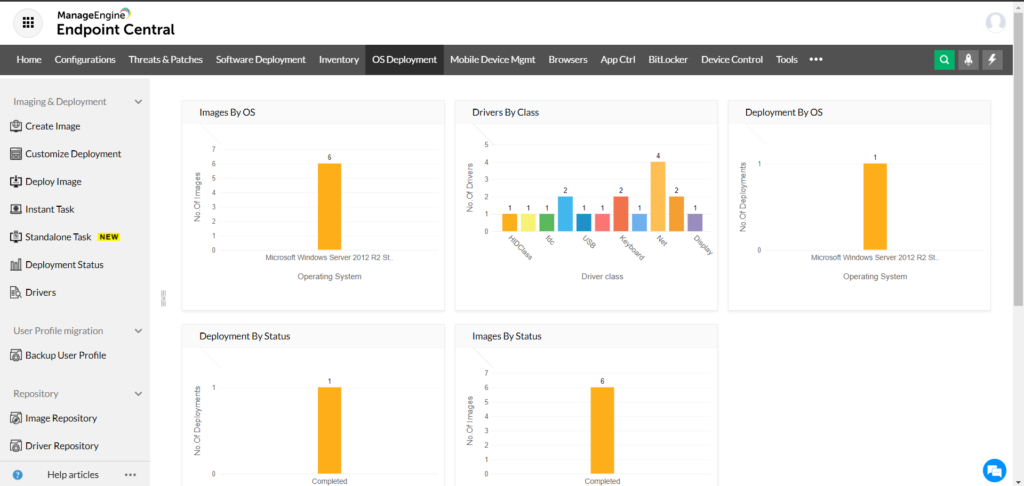
- IT Asset Management: Track and manage software and hardware assets, including license and warranty tracking.
- Unauthorized Device Restriction: Regulate and restrict stray peripheral devices, and closely monitor file transfers in and out of the network.
- Data Loss Prevention: Implement advanced strategies to protect critical enterprise data from disclosure and theft.
- OS Imaging and Deployment: Automatically image and deploy operating systems on Windows computers with required drivers and applications.
- App Management and Distribution: Deploy software to all endpoints, block or allow applications with rule-based filtering.
- Endpoint Privilege Management: Manage privileges, monitor apps, and control sensitive data at the endpoint level to mitigate insider threats.
- Advanced Remote Troubleshooting: Remotely connect with end users to solve issues in real-time.
- Configuration Management: Ensure endpoints comply with policies and industry practices by managing configurations.
- Browser Security: Monitor and enforce security measures on browsers used in the organization.
Platform Support:
Endpoint Central supports a wide range of devices and operating systems,

Pricing:
ManageEngine offers different editions of Endpoint Central with varying features to cater to different business needs.
The pricing plans include:
- Professional Edition: Starts annually at $795.
- Enterprise Edition: Starts annually at $945.
- UEM Edition: Starts annually at $1,095.
- Security Edition: Starts annually at $1,695.
Cloud Pricing
- Professional Edition: Starts annually at $1045.
- Enterprise Edition: Starts annually at $1245.
- UEM Edition: Starts annually at $1,395.
- Security Edition: Starts annually at $2,045.
Each edition comes with a free trial option, allowing businesses to evaluate the software before making a commitment.
Industry Reports:
Endpoint Central has received recognition from prominent industry reports, including :
- Gartner: Recognized in the 2022 Magic Quadrant.
- ManageEngine was recognized as an overall leader in KuppingerCole Leadership Compass 2023 for Unified Endpoint Management for the second consecutive year.
- IDC: Leader in the 2022 IDC MarketScape.
- Forrester: Strong Performer in 2023 Forrester Wave
 .
.
These acknowledgements reflect the software’s standing in the market and its capabilities.
Differentiation:
Endpoint Central enhances a conventional desktop management service by providing increased depth and customization. It enables the automation of routine endpoint management tasks, such as patch installation, software deployment, imaging, and OS deployment.
Additionally, the platform facilitates the management of assets and software licenses, monitoring software usage statistics, controlling USB device usage, and assuming command over remote desktops.
Endpoint Central provides a variety of security functionalities, encompassing ransomware protection, prevention of data loss, security for applications and devices, browser security, vulnerability management, endpoint privilege management, and the management of BitLocker.
Customer Testimonials:
Several well-known enterprises, including IBM, Honeywell, Dell, Charter, Pinterest, Disney, and Xerox, trust ManageEngine Endpoint Central. Customer testimonials highlight the software’s effectiveness in areas such as patch management, security, and employee support.
- Hector Camejo, an ICT & Service Desk Plus Administrator, emphasizes the fantastic outcome of patch management and remote features.
- Mihir Patel, an IT Infrastructure Manager at E-store logistics, notes how Endpoint Central has enhanced employee experience and efficiently supported users.
Anticipating the Future with Endpoint Central:
As we cast our gaze into the future, it’s evident that the industry is steering towards a hybrid landscape, a harmonious blend of on-premises and cloud instances, a coexistence of virtual and physical machines, and a workforce dynamic that spans traditional offices and distributed remote setups. The beauty is, that ManageEngine’s Endpoint Central is not just keeping pace with these changes but is poised to excel in this diverse scenario.
From a reviewer’s standpoint, it’s promising to witness Endpoint Central’s readiness for the shifting tides. While our insights may not capture every detail, it’s noteworthy that their roadmap includes a seamless integration of Endpoint Security Management and UEM.
This strategic move indicates a proactive approach to address the evolving needs of users. The commitment to enhancing features aligns with the dynamic nature of the IT landscape, showcasing a dedication to staying ahead of the curve. For businesses navigating the complexities of the hybrid future, Endpoint Central appears to be a robust and forward-thinking solution.
Final Verdict on ManageEngine Endpoint Central
ManageEngine Endpoint Central stands out as a comprehensive UEM solution with a robust set of features, broad platform support, and industry recognition. Its ability to address diverse IT management needs, coupled with positive customer testimonials, and affordable pricing, makes it a strong contender for businesses looking to streamline and secure their digital workplaces.
The software’s commitment to privacy, long-term partnerships, and tailored pricing plans further contribute to its appeal in the competitive IT management landscape.
]]>To ensure improved security and vigilance, endpoint security is a key aspect for a business and personal user. In this article, we’ll see some insights on endpoint security, its importance and the options you can explore.
What is Endpoint Security Software?
Endpoint security is the process of protecting your desktops, laptops, mobile devices, browsers, users and any other plug-in devices associated with the primary endpoints from external threats. With modernization of technology, the malicious actors and their attack vectors are equaling evolving.
Businesses and end-users need robust endpoint security software to protect their devices from spear phishing, backdoors, Trojan horse, worms, ransomware, spyware, adware and other nefarious threats from unknown entities.
This system that protects endpoints from external attacks and ensures the safety of devices and data associated with it is called Endpoint Security Software.
Why will Endpoint Security Software make a difference?
With evolving threats, attackers can automate and orchestrate attacks with a high level of customization and accuracy yielding better results for their cyber-threat campaigns. Especially with the support of bots in the DDOS attacks, hackers can manipulate the targeted endpoints in several directions until their goal is achieved.
With endpoint protection software, businesses can detect, prevent, identify, analyze and take action in a more efficient way as they only need time to fix the issue and not identify it. Endpoint Security Tools are a vital part of IT teams and MSPs for their efficient service and management.
How to choose the right Endpoint Security Software for your network?
While evaluating the options in the market we must know the key capabilities to look for in a endpoint security software. These key features are the fundamental for a efficient endpoint protection tool that will give businesses and IT professionals an upper hand against cyber criminals.
The five key endpoint security features to look for,
- Threat Protection
- Automated Detection and Remediation
- Alerting and Reporting
- Device and Application Control
- Data Security and Data Loss Prevention
Threat Protection
Identifying threats is a critical aspect of endpoint security, and the software you are evaluating must be able to detect and respond to advanced threat vectors including emails, phishing, malicious sites and downloads, malicious programs, and more.
Automated Detection and Remediation
While alerting is important, the endpoint security software should go one step ahead and be able to remedify the security issue without manual intervention of security professionals automatically. This is another important feature as threats are mostly hyper-fast and waiting for security professionals to handle it will only make things worse for a business and better for threat actors. Your endpoint protection software should detect and fix threats automatically unless a special use case is triggered.
Device and application control
Managing and monitoring devices and their applications are a need of the hour, as any threats deployed into your network are mostly associated with either of these. Control over devices and applications is needed to scrutinize the security layer of devices and to ensure there are zero unprotected devices and the right detection and authentication protocols are in place.
Data loss prevention
Cyber-attackers will breach into your network, access your data, encrypt, delete or extort data for additional benefits. Hence, your endpoint security tool must be able to prevent data being extorted or encrypted.
It should act both proactively and reactively to understand the attack vector, act accordingly to counter the threat and ensure your business critical files are secured all the time. Data transfer to external network must be alerted and permitted only after approval from the right individuals.
Alerting and reporting
Any anonymous security events have to be monitored and alerted by the endpoint security software. The events have to be monitored, recorded and reported for a periodic analysis, which will help IT teams see a pattern and take necessary measures to reduce the event in future. The reporting must be detailed information of the events for better decision-making.
Endpoint Security Software Market Analysis
The Endpoint Security tool market is always evolving with competitive vendors and amazing features every year. Choosing the right endpoint protection software for your business could be challenging, especially if it is your first time evaluating the endpoint security tools directly.
In this article, we have evaluated the products from both primary and secondary research to give you first hand information about the tool that will suit your network.
As per Gartner research, the endpoint security market contains several players in the Leaders, Challengers, Visionaries and Niche Players categories. However, we will only be looking at the Leaders as there are six active players that have been included in the Leaders category of the Endpoint Protection Platform Magic Quadrant.
Top 6 Best Endpoint Security Software for 2024 – Best Endpoint Protection Software
As per Gartner Magic Quadrant, Leaders “have broad capabilities in advanced malware protection, and proven management capabilities for large enterprise accounts. Increasingly, Leaders provide holistic XDR platforms that allow customers to consolidate their other tools and adopt a single-vendor solution.”
Microsoft Endpoint Security Software – Microsoft 365 Defender
Microsoft 365 Defender provides Extended Detection and Response(XDR) capabilities for endpoints, cloud applications, emails and business documents. It uses AI to identify, detect and alert IT teams for critical alerts.
The self-healing technology automates remediation more than 70% of the time, ensuring IT teams can focus on other high priority tasks.
Microsoft Endpoint Security Software Defender 365 had some nice enhancements recently.
- Improved mobile threat defense capabilities for iOS and Android is moved to GA.
- Microsoft now delivers endpoint protection across all major OS platforms.
- Improved macOS support with the inclusion of threat and vulnerability management.
- Protection from phishing attacks for users who have access to the most critical information. Customers can customize account workflows to offer these users an extra layer of security.
- The addition of Azure Defender and Azure Sentinel are another major green flags to choose Microsoft over other options.
Microsoft offers deeply integrated Security Information and Event Management(SIEM) and XDR for end-to-end visibility and prioritized actionable insights across all your enterprise assets.
Pricing: $60 per user per year
Crowdstrike Endpoint Security Software – Falcon
CrowdStrike provides a flexible and extensible platform Falcon. It provides a variety of options and capabilities like Falcon Insight, Falcon Discover, Falcon Prevent, Falcon Device Control, Falcon Firewall Management, etc.
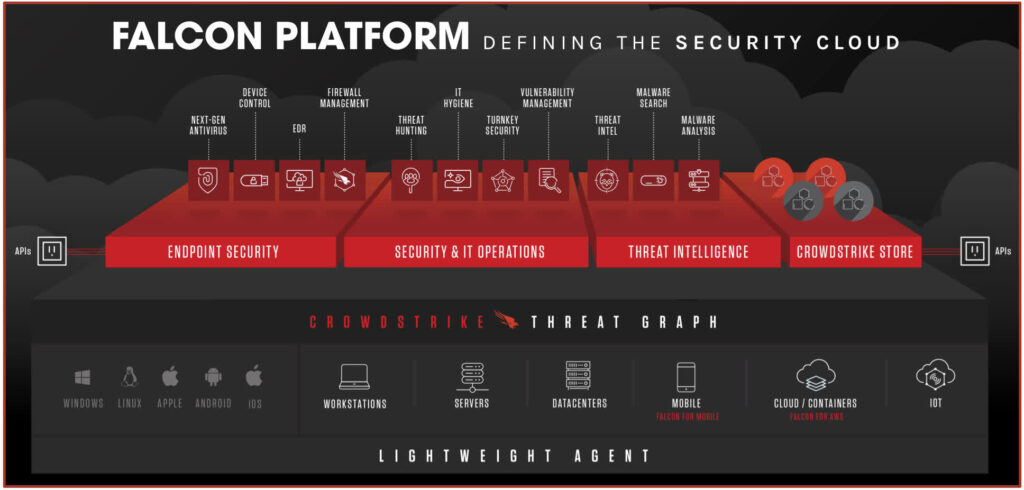
Crowdstrike endpoint security tools are tailor-made for customers working with more stringent compliance or operational requirements.CrowdStrike offers products like Falcon Pro, Falcon Enterprise, Falcon Premium, and Falcon Complete.
Features:
- Automated threat hunting, alerting and reporting.
- Endpoint threat detection, protection and expanded visibility.
- Cyber intelligence against threats for immediate response.
- Device monitoring and control
Pricing: $59.99 per endpoint per year
Trend Micro Endpoint Security Tool – ApexOne
Trend Micro Endpoint Security Software comes with advanced threat detection and response system against modern threats including fileless and ransomware attack vectors.
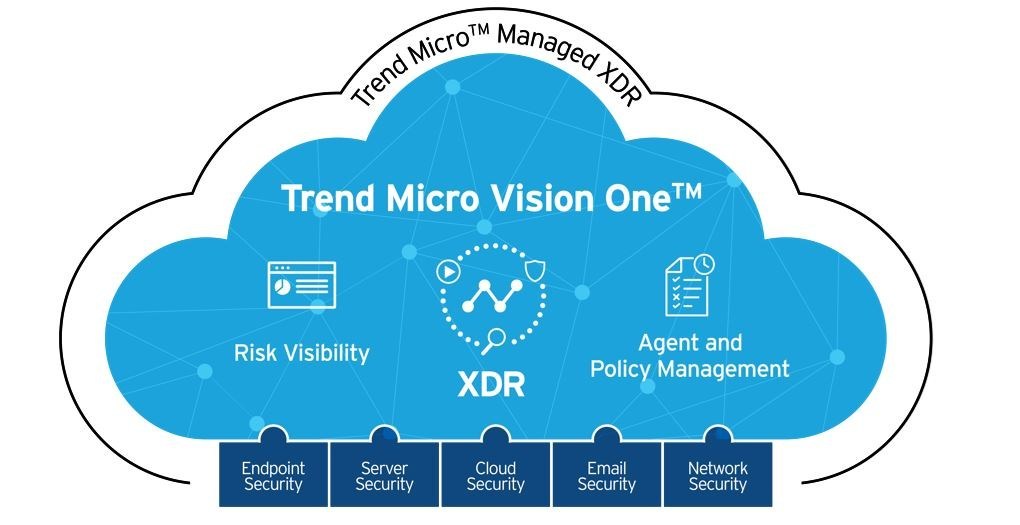
Provides insights, initiating investigation when needed, visibility over a unified EDR tool-set, managed detection and response from a singe agent.
Features:
- Strong SIEM integration
- Open API Set
- Cross generation blend of advanced techniques
- Pre-execution and runtime machine learning
- Fileless, living of the land and ransomware detection capabilities
- Ability to reduce false positives
- Protection against scripts, injection, ransomware, memory, and browser attacks through innovative behavior analysis
Pricing: $39.95 per endpoint per year
SentinelOne Endpoint Protection Software
SentinelOne Endpoint Security Tool offers protection against most of the cyber threats with Singularity XDR approach. It works on a static AI engine that will assist in precautionary detection and protection of your network.
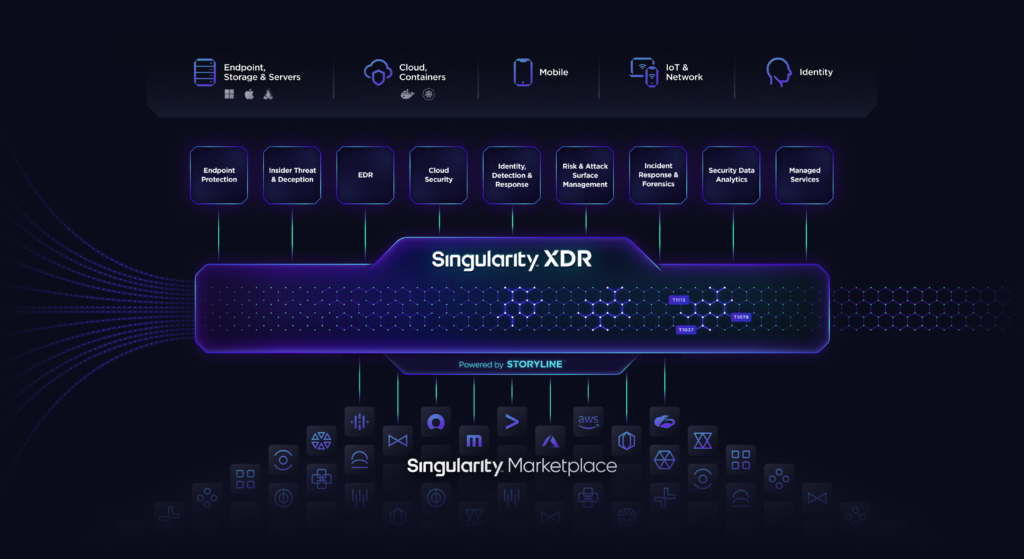
Comes with seamless data ingestion, flexibility, cross-stack visibility, integration with other security tools, and automation.
Features:
- Protection against threats and modern attack vectors
- File ingestion and analysis
- Lightweight agent
- Singularity XDR – A unified approach towards EDR and XDR.
Pricing: $45 per endpoint per year
McAfee Endpoint Security Software – Trellix Endpoint Protection
McAfee Endpoint Protection Tool comes with amazing capabilities that will allow IT professional to perform on-demand scanning, containment of applications, behavior monitoring, rollback remediation, firewall management, web security management and integration with MVISION MDR for further enhancements. McAfee Enterprise and FireEye combo is now known as Trellix.
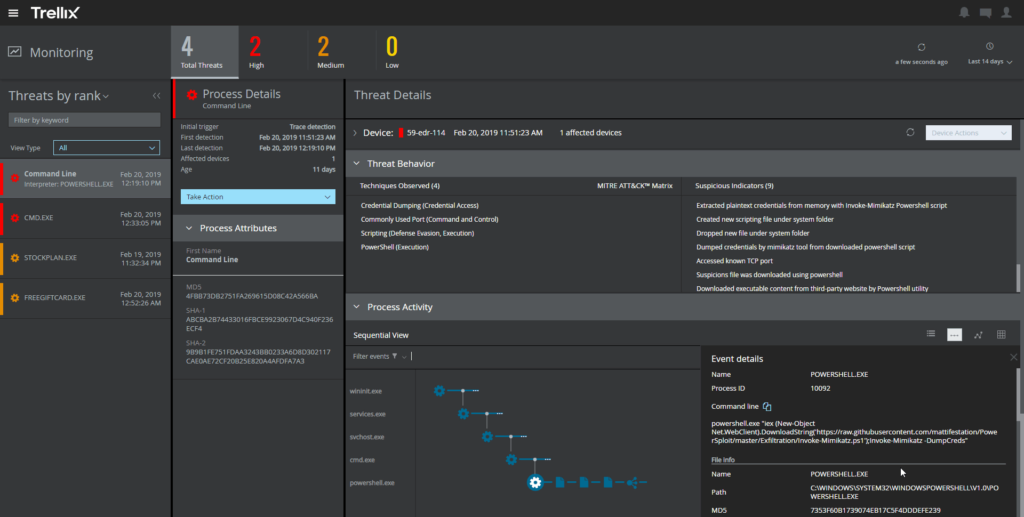
Features:
- Advanced defenses for advanced threats
- Machine learning enables to be adaptive to modern threats and patterns
- Single pane of glass approach for all your endpoint security needs
- MVISION insights for swift and high-priority case handling and remediation
Pricing: $31.06 per endpoint per year
All the above-mentioned endpoint security software are the best in the market as per Gartner, G2 Crowd, Software Advise, Capterra and our own analysis and testing of the tools and their capabilities.
The pricing is almost similar for the vendors except for the case of McAfee. If your evaluating endpoint protection tools, I would suggest you map your requirements to the features provided by the vendors and also calculate your budget and the price of the licenses.
ManageEngine Vulnerability Manager Plus
ManageEngine Vulnerability Manager Plus is a robust solution for bolstering endpoint security. It boasts features such as automated vulnerability assessment, timely threat intelligence updates, and seamless integration with existing security systems. The platform’s user-friendly interface simplifies the complex task of managing vulnerabilities, enabling IT teams to be efficient and productive.
Vulnerability Manager Plus stands out with its competitive pricing model, aligning with budget-conscious clients without compromising on quality. Customer reviews highlight its efficiency in identifying and addressing vulnerabilities promptly, contributing to a heightened sense of security.
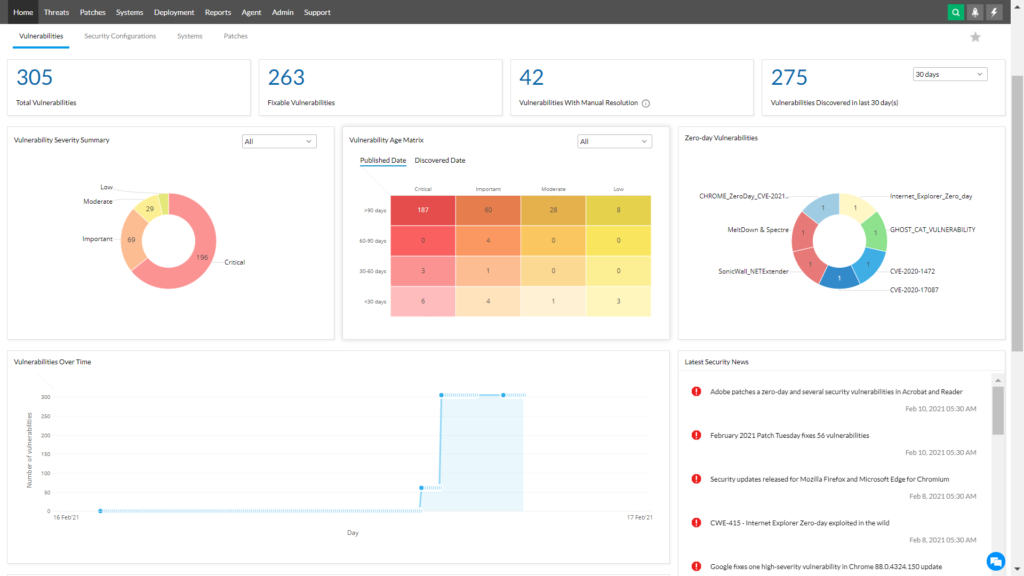
Features:
- Automated vulnerability assessment
- Timely threat intelligence updates
- Security configuration management
- Web server hardening
- Zero-day vulnerability mitigation
- Antivirus audit
- Patch management
Pricing: 100 workstations and single-user license starts at $1195
Honorable Mentions – Best Endpoint Protection Software 2024
Sophos Endpoint Protection Tool
Sophos Endpoint Security Software is another key vendor in the list of Leaders as per Gartner Magic Quadrant and we agree to that. Sophos provides MDR, EDR, XDR, Zero-Trust approach, Central management and anti-ransomware protections. The pricing is around $45 per endpoint per year.
Give a try on all these endpoint security software vendors, evaluate them for your network and see which suits your ecosystem and demands better. Endpoint Protection Software are crucial part of enterprises and SMB’s as their presence will avoid major damages to their business operations.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, and Twitter.
You can reach out to us via Twitter/ Facebook or mail us at admin@thecybersecuritytimes.com for advertising requests.
]]>