However, the restaurant owner was smart enough to identify the fraudsters and reported the incident to the police. A first information report (FIR) has been filed by the police and further investigations are being done.
What is Paytm app and how is Paytm Spoof different from it?
Paytm is India’s number one digital payment app, that is being used by more than 30 crore Indians. The app is used for all sorts of payments, bills, transactions including UPI transactions. After the demonetization that happened in India on 2016, the digital currency and payment domain saw a nice boon which made payment apps like Paytm, Google Pay, Phonepay and others saw an amazing growth.
Considering the wide usage of Paytm, three fraudsters started exploiting it by using a bogus Paytm looking app called Paytm Spoof. This app will allow fraudsters to create fake payment receipts that can be used to evade bills. This app is not available on Google Play and only can be downloaded by direct API links through the web.
Breaking down the Paytm Spoof app
The Paytm Spoof that can be downloaded only via APK when downloaded and installed can help fraudsters create a fake transaction page that can be customized with the merchant name, billing amount, Paytm wallet balance, transaction ID, Paytm ID and other basic details to make the payment page look legitimate and evade the billing counters.
As we know, the Paytm app is used by scanning the QR codes in the merchant outlets, the fraudsters used this moment to identify the merchant details and then use the same to create their customized payment page and manipulate merchant owners to believe that they have paid with the exact bill amount. The below image will depict the fraud perfectly,
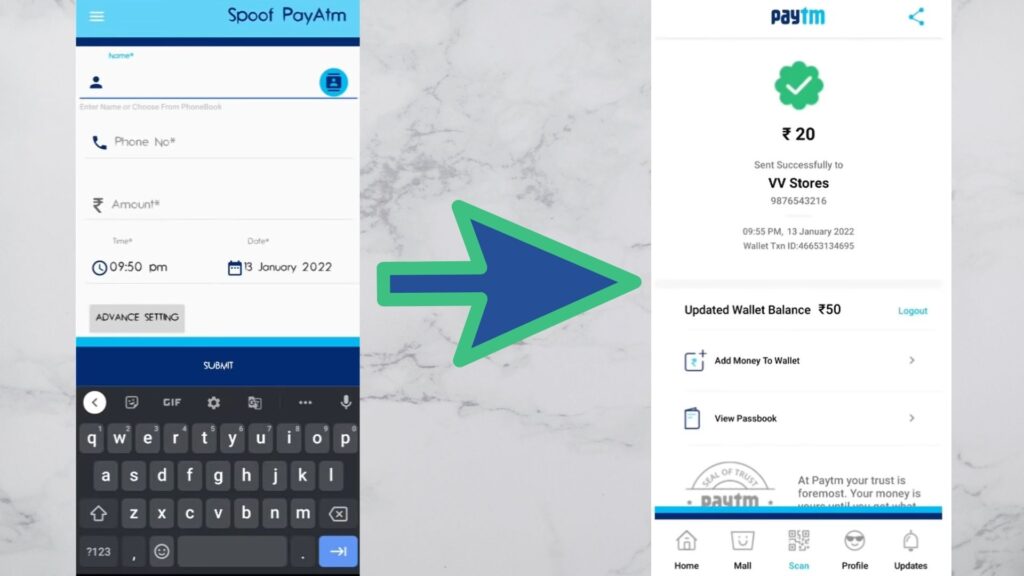
How to be vigilant against Paytm Spoof fraud?
Always check for the amount being transferred to your merchant or savings account before allowing the person to leave. If possible try to see if they the phone that is scanning the QR code and making the payment is same, though this might not be full vigilant, keeping an eye on their behavior and action can make them nervous, help us figure out if something is fishy.
This ain’t social engineering, or a cyberattack but a simple payment manipulation just like how fake cash notes were used to escape payments in counters.
Check for money transfer confirmation notifications and please keep your push notification turned ON for easy confirmation. You can also use Paytm Sound Box that sends audio confirmation whenever payment is made.
And for others downloading Paytm app, always download apps from Play Store and App Store, do not google the app and install the apps directly via APK files. People who are aware of the basic cyber hygiene may not fall for this APK trap but for others this is a very important best practice as anything outside of the Play and App store isn’t safe and could cause harmful effects on your device and data.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, Instagram, Twitter and Reddit.
You can reach out to us via Twitter or Facebook, for any advertising requests.
]]>