What is ManageEngine Vulnerability Manager Plus?
ManageEngine Vulnerability Manager Plus is a multi-OS vulnerability management and compliance solution designed to provide end-to-end coverage, continual visibility, rigorous assessment, and integral remediation of threats and vulnerabilities.
It serves as a centralized console, making it an indispensable tool for empowering distributed workforces with secure working conditions.
Why Business should employ ManageEngine Vulnerability Manager Plus?
- 360-Degree Visibility: Gain insights into vulnerabilities, security misconfigurations, high-risk software, and web server misconfigurations across local and remote endpoints.
- Attacker-Based Analytics: Leverage analytics to prioritize areas more likely to be exploited by attackers, ensuring a focused and efficient vulnerability management approach.
- Platform Support: With support for Windows, Linux, and macOS (patch management only), Vulnerability Manager Plus is a versatile solution for various operating systems.
Vulnerability Manager Plus Architecture Overview:
At Zoho Corp. Site, an External Crawler continuously probes the internet, gathering crucial vulnerability information. This includes CVE ID, CVSS scores, severity details, exploit code, and patches. The Central Database, hosted on the Zoho Corp. site, acts as a repository constantly updated with the latest details on known and emerging vulnerabilities, patches, security configurations, web server hardening content, high-risk software lists, and compliance policies.
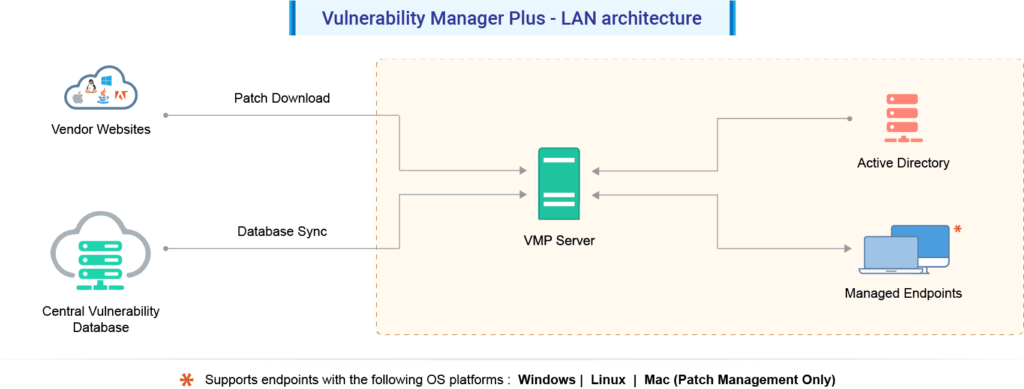
At the customer site, the Vulnerability Manager Plus Server, along with lightweight agents and a user-friendly web console, forms the core components. The server, subscribing to the Central Vulnerability Database, orchestrates tasks such as installing agents, scanning for vulnerabilities, deploying patches, and maintaining continuous communication, ensuring effective vulnerability management across the enterprise.
Features & Capabilities
- Vulnerability Assessment: Identify real risks based on exploitability, severity, age, affected system count, and fix availability.
- Compliance: Audit and maintain systems in line with 75+ CIS benchmarks, instantly identifying violations and offering detailed remediation insights.
- Automated Patch Management: Customize, orchestrate, and automate the patching process for Windows, Mac, Linux, and over 850 third-party applications.
- Vulnerability management for network devices: Strengthens network device security by creating a centralized inventory, executing scans for firmware vulnerabilities, and applying the latest patches to fix vulnerabilities.
- Security Configuration Management: Optimize system security by enforcing complex passwords, least privileges, and compliance with CIS and STIG security guidelines.
- Web Server Hardening: Obtain details on web server security flaws, helping establish and maintain secure servers resistant to various attack variants.
- High-Risk Software Audit: Identify and uninstall unauthorized and unsupported software, enhancing endpoint security.
- Zero-Day Vulnerability Mitigation: Deploy pre-built, tested scripts promptly to secure the network from zero-day vulnerabilities without waiting for patches.
Platform Support
- Windows: Vulnerability management software for Windows.
- Linux: Vulnerability management software for Linux.
- Mac: Limited to patch management for macOS.
For a detailed understanding of the Platform support, please take a look at the OS comparison matrix.
Pricing
ManageEngine Vulnerability Manager Plus is available in three editions:
- Free Edition: Suitable for SMBs, fully functional, managing up to 25 endpoints free forever.
- Professional: Suitable for computers in LAN, offering vulnerability scanning, system misconfiguration detection, and more – Starts at $695 for 100 Workstations and Single User License Annually.
- Enterprise: Suitable for computers in WAN, including all Professional Edition features, with additional capabilities like secure configuration deployment, compliance, automated patch deployment, and more – Starts at $1195 for 100 Workstations and Single User License Annually.
For a detailed comparison of the editions, please check the Edition Comparison Matrix.
Future of Vulnerability Manager Plus
In the ever-evolving landscape of cyber threats, adapting vulnerability management tools is paramount. ManageEngine stands at the forefront of this evolution, poised to meet the challenges of the future head-on. With a commitment to staying ahead of emerging threats, ManageEngine Vulnerability Manager Plus ensures the resilience of organizations in the face of dynamic cyber risks.
The foundation of ManageEngine’s future-proof approach lies in its provision of insightful reports that offer a comprehensive understanding of an organization’s security posture. By arming businesses with detailed and actionable insights, ManageEngine enables informed decision-making to fortify defenses effectively.
Moreover, ManageEngine’s proactive security measures set it apart in the fight against evolving threats. Through continuous updates and enhancements, the platform anticipates and addresses vulnerabilities before they can be exploited, fostering a proactive rather than reactive cybersecurity stance.
In conclusion, ManageEngine’s commitment to providing insightful reports and implementing proactive security measures positions Vulnerability Manager Plus as a robust solution ready to navigate the intricate landscape of future cyber threats successfully.
Final Verdict on ManageEngine Vulnerability Manager Plus
ManageEngine Vulnerability Manager Plus is an essential tool for businesses serious about maintaining a secure digital environment. With its comprehensive features, multi-OS support, and user-friendly interface, it stands out as a reliable solution in the vulnerability management space.
In conclusion, businesses looking to fortify their cybersecurity posture should consider ManageEngine Vulnerability Manager Plus for its robust capabilities and proven track record.
]]>With a vulnerability management tool, companies can ensure their network security is always updated and can ensure better protection of assets overall.
In this article, we’ll see how vulnerability management software can facilitate enterprise network security and ensure their data is protected from external threats.
What is Vulnerability Management Software?
The process of scanning an entire network to identify vulnerabilities and provide remediation to fix the situation and the vulnerability, say it be temporary or permanent, and ensure such threats are detected in advance and fixed promptly is called Vulnerability Management.
The tool that facilitates the whole process by allocating degrees or levels of critical vulnerabilities is called the Vulnerability Management Software. This is a proactive cybersecurity tool and is different from antivirus and firewall which are reactive tools.
Why will Vulnerability Management Software make a difference?
Attackers often exploit the existing vulnerabilities in any organization. They try to exploit the zero-day vulnerabilities, port vulnerabilities, device vulnerabilities, or firmware vulnerabilities to breach network security and exploit the data associated with those devices and their connected applications.
When companies employ a vulnerability scanner and vulnerability management software, they are ready for external attacks with robust security in place. Attackers won’t find the loopholes and their attempts will only fail.
How to choose Vulnerability Management Software?
While evaluating the options in the market we must know the key capabilities to look for in a vulnerability management software. These key features are fundamental for an efficient vulnerability management tool that will give businesses and IT professionals an upper hand against cyber criminals,
- Vulnerability Scanner
- Detection and Description of vulnerabilities
- Patch management
- Custom scripts for zero-days
- Alerting and Reporting
Vulnerability Scanner
The vulnerability management software must come with an effective vulnerability scanning agent that should cover all the network devices and endpoints holistically. The range of coverage is important as it determines the vulnerability spread across the enterprise network.
Detection and Description of vulnerabilities
Companies need to detect and identify vulnerabilities at the right time to avoid their exploitation affecting their network and the data associated with it. A vulnerability management software should be able to identify and also give a brief description of the vulnerability to enable IT security professionals and the SOC team to understand and act on it accordingly.
Patch management
Vulnerability management should come along with patch management as patching is the remediation stage after detection.
Custom Scripts for Zero-Days
Not all vulnerabilities come with vendor patches as soon as they are reported. When there is no patch available, the SOC team must be able to do a workaround for the same and deploy a custom script to mitigate the situation temporarily until a patch is officially released.
Alerting and Reporting
The vulnerability management tool should have user-friendly alerting of vulnerabilities. The alerts should give the details of the CVE and their description, if patches are available then should include that as well. The reporting should be automated and should support the breakdown of the vulnerability management process.
Top 6 Vulnerability Management Software – Best Vulnerability Management Tool for 2024
Vulnerability management tools should be an integral part of any company, and to do that here are the best five vulnerability management software that you can evaluate and choose from.
Tenable Vulnerability Management Software – Vulnerability Management Tool
Tenable provides visibility into all the devices and assets in the network, including vulnerabilities across the entire attack surface. This allows companies to assess everything, since malicious actors are already scanning your corporate network, it is good to do the same with Tenable as well.
The Tenable vulnerability management tool employs threat intelligence to detect and predict vulnerabilities that are critical to the network. Furthermore, the tools also showcase the description of the vulnerability with key metrics and insights for further action.
Price: $2275/year for 65 devices. 41497
Heimdal Security – Vulnerability Management Tool
Heimdal Security comes with automated patch management that will deploy and patch any Windows, Linux and third-party software across networks, branches and geos. Gives complete visibility into the granular control over entire software inventory. Update applications located anywhere in the world from one central location.
Offers unified threat intelligence that comes with DNS filtering, next-gen antivirus, ransomware encryption protection, remote desktop control, email security, email fraud prevention, and privilege access management.
Price: 16/year
ManageEngine Vulnerability Manager Plus:
Enhance your enterprise’s security with Vulnerability Manager Plus, a multi-OS solution offering end-to-end vulnerability management and compliance with built-in remediation. Ensure comprehensive coverage, continual visibility, and rigorous assessment from a single console.
ManageEngine Vulnerability Manager Plus ensures robust security with features like comprehensive Vulnerability Assessment, effortless Compliance meeting 75+ CIS benchmarks, streamlined Patch Management for Windows, Mac, Linux, and 500+ third-party apps, enhanced Security Configuration Management, effective Web Server Hardening, swift High-Risk Software Audit, and prompt Zero-day Vulnerability Mitigation. Strengthen your security effortlessly.
Pricing: Starts at $1195 for 100 workstations annually.
Netsparker vulnerability management software – Invicti vulnerability management tool
Invicti Netsparker vulnerability software is an automated vulnerability management tool that scans web applications and services to detect vulnerabilities in their security. The scanning includes all applications, regardless of operating system.
The tool combines DAST and IAST for scanning to detect vulnerabilities. It is behaviour-based and signature-based and gives you accurate results on time. It is a ‘Proof Based Scanning’ feature that can automatically detect vulnerabilities to identify if they are false positives or real ones.
Price: $666/month.
Acunetix vulnerability management tool
Acunetix vulnerability management software can be deployed to scan and secure all types of websites and web applications. With Advanced Macro Recording feature that offers sophisticated multi-level forms of security. It is known to have identified 7000 vulnerabilities including databases, weak passwords, XSS and more.
The tool also reduces false positives as it double-checks vulnerabilities before reporting it to the subject of concern. It facilitates automated and scheduled scans ahead of time as per business requirements.
Price: $4495 per website
SecPod vulnerability management software
SecPod SanerNow Cyber hygiene is an automated and advanced vulnerability management tool that brings a new revolution to traditional patching. The integrated vulnerability assessment and patch management make the entire vulnerability management hassle-free. Detection of CVE vulnerabilities with instant mitigation and remedies makes SecPod unique and the best option for SMBs.
Supports major OS and devices with support for routers and switches. The unified console for vulnerability assessment and remediation makes the SecPod vulnerability management tool user-friendly.
Price: $50/year per device.
Give a try on all these vulnerability management tools, evaluate them for your network and see which suits your ecosystem and demands better.
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, and Twitter. You can reach out to us via Twitter/ Facebook or mail us at admin@thecybersecuritytimes.com for advertising requests.
]]>Indeed, there is no domain without phishing. This still and will remain a critical threat to individuals, businesses, organizations, and their financial cum personal accounts. Ultimately, brands can lose their reputation among the elite corporate communities. Overall, this social engineering strategy, along with the phishing simulation tools, is quite interesting to read. Check them from down below.
What is a Phishing tool?
You must have come across articles like these – where an official-looking or site email asks for a credit card or PAN number for verification. Nevertheless, that is a malicious prompt from some phishing tools. Victims unknowingly disseminate their confidential information and ultimately get caught in grave financial and personal troubles.
According to the Federal Trade Commission (FTC), phishing tools attack profiles by either of these means;
- An email might require a signature from you to acknowledge a fake invoice.
- An illegitimate company may offer you exclusive coupon codes and bonus offers.
- An unused, age-old account may notify you to update your personal information.
- An illicit site can claim it noticed suspicious activity and requires your re-login.
So, your awareness to detect phishing tools and their deceitful messages is paramount to digital safety!
Types of Phishing Attack
“Fishing” passwords happen in 15+ ways with various phishing simulation software available. Yet, these are the five phishing attacks that are oftentimes witnessed these days;
- Spear Phishing – This electronic communications scam is a threat to get private data from the victim; not just by acting legitimately but also the criminal tries to install malware on a targeted user’s computer.
- HTTPS Phishing – With the facility of Hypertext transfer protocol secure (HTTPS), scammers add a short-tail HTTPS code to their website and make the victims perform certain actions on the page.
- Deceptive Phishing – An untrustworthy email gets sent bulk to multiple sources. The purpose of such a misleading technique is to put a “Call To Action” (CTA) and get the recipient’s details, like bank account details.
- Pharming – A victim’s DNS server gets negotiated for redirecting them to a simulated website that steals their private information, even without making them click on a button.
- Whaling – Masquerading as a legal source, whaling is a phishing attack where only high-level senior executives are targeted to initiate steps, like wire transfer of funds.
The end intent of phishing is to hack and steal passcodes and specifications by faking as legitimate sources. Only the way of pretending and mode of communication varies accordingly. And hence your knowledge of using phishing simulation tools is a must!
Why is Phishing Simulation software important?
Recognizing, dodging, and reporting potential data threats is critical to both the common man and a business firm. Owing to that, we can stay protected to a possible extent by using phishing simulation software.
As the name states, create a ‘simulated’ environment and verify where and how our information is phish-able, probably. Even exclusive security training programs are conducted for employees to make them aware of these phishing tools.
Benefits of Phishing Tools
As a part of security awareness, we can build defensive human resources by understanding the depths of any phishing simulation software. Regardless of how big a corporation is, there would be minute security gaps. And software modules like these will help us detect and bridge those gaps.
Also, the key to using such phishing tools is to seriously reduce the overall cost spent when at times of a real cyberattack.
Top 5 Best Phishing Tools for 2024
So, ready to keep your personal information safe? Then, get to know about the features of the top 5 phishing simulation tools listed below;
SEToolkit
If speed is your concern, then SEToolkit is your thing. From a mastermind ‘Dave Kennedy’ from ‘TrustedSec’, the Social-Engineer Toolkit is an open-source penetration testing Python framework. From fake phone numbers to dummy SMS messages, personalize anything important and attack instantly, free of cost.
Besides phishing, you can use SEToolkit even for Infection Media Generator, QRCode Attacks, and Arduino-Based Attack.
Give a try on these phishing tools and experience this phishing simulation software.
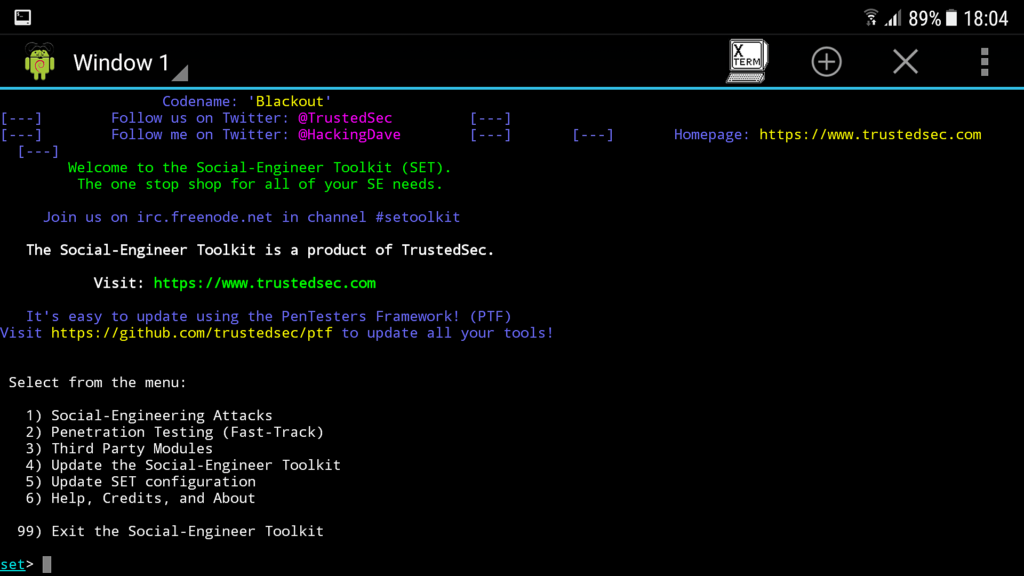
Highlights
- Multiple tweaks from the configuration menu.
- Custom attack vectors.
- Integration support with third parties.
- Multi-platform: Runs on Linux, Unix, and Windows.
King-Phisher
Unlike the other complicated phishing tools known, King-Phisher has a user-friendly appearance. You can get 100% control over both the server content and emails with its extremely flexible architecture. If you operate a firm, then you need to get explicit permission before obtaining the database.
However, with a legal permit, you can make wonders with King-Phisher, owing to its alerts, options, and web page cloning capabilities.
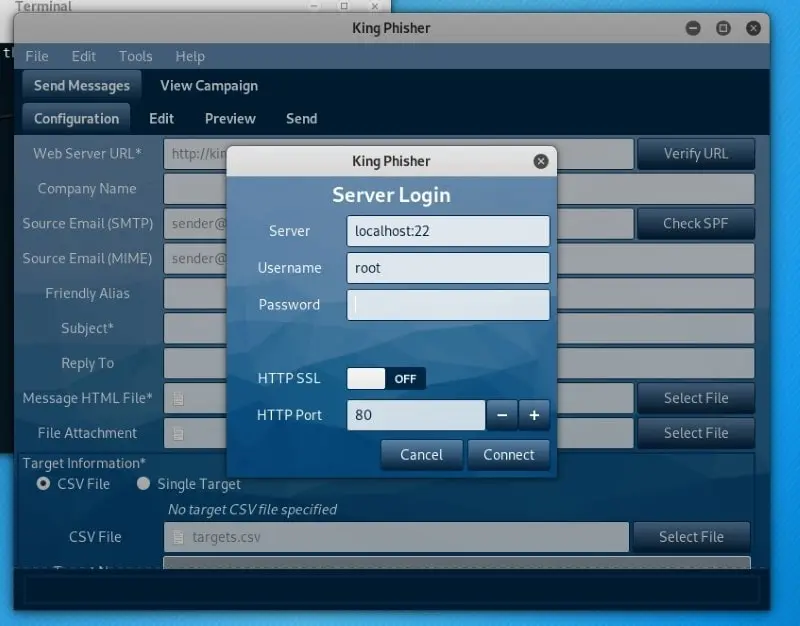
Highlights
- Run multiple phishing campaigns simultaneously.
- Geolocation of visitors.
- Credential harvesting from landing pages
- Integrated Sender Policy Framework (SPF) checks
Give a try on these phishing tools and experience this phishing simulation software.
Evilginx2
With the aid of session cookies, the Evilginx2 phishing tools utilize the man-in-the-middle attack framework. It acts as a relay between the phished user and the actual website. You can even bypass the 2-factor authentication (2FA) protection. Since the entire program is pre-written in GO (as a standalone app), your setup is going to be simple. As of date, there are no vulnerabilities reported with its dependent libraries.
Highlights
- Customizable hostnames for each phishing lure.
- Generated URLs are exportable to file (text, CSV, JSON).
- IP black-list with automated address black-listing option.
- SOCKS5 and HTTP(S) proxy support routing connections.
Give a try on these phishing tools and experience this phishing simulation software.
HiddenEye
HiddenEye is a contemporary tool, well-suited for regular phishing and keyloggers (keystroke logging). The functional components and its brute force attack techniques are so good. 30+ famously global social media channels such as Instagram, Yahoo, Facebook, Snapchat, etc., can be easily phished. You need to have the Termux or UserLand application if you are an Android user.
Highlights
- Multiple Tunneling Services.
- Serveo URL type selection (between Custom and Random URLs).
- Live attacks with IP, geolocation, ISP, country, address, etc., are possible.
- A highly efficient tool for Enterprise level Penetration Test.
Give a try on these phishing tools and experience this phishing simulation software.
Infosec IQ
With its 1,000+ realistic phishing templates, Infosec IQ is an all-purpose name for both data breach simulation as well as security awareness training. Typosquatting, domain-specific spoofing, and similar tactics work here.
Generate your company’s initial phish rate for free, but at later use, you need to pay. Once done, you can even replicate in-the-wild, authentic attacks using real brand logos.
Highlights
- Around 300 international phishing templates are available with translated versions.
- USB, malware, business email compromise (BEC), malicious attachments, and more.
- Team quarantine features are available for actual incidents.
- Training modules can be pre-scheduled even for one full year.
Give a try on these phishing tools and experience this phishing simulation software.
Honorable Phishing Simulation Tools for 2024 – Best Phishing Tools
Three other phishing modules are getting quite popular with the penetration testers, blue and purple teams of this gen, and here they are;
SocialFish
Known for its customizable links, SocialFish is one of the classic phishing simulation tools for convincing results with social media phishing. Its present version 3, plus the BSD-3-Clause License, make it ever-ready to harvest multiple LANs.
Python 3.6 or Greater and Pip3 are prerequisites to its installation. Above all, the biggest perk is that you can clone social media sites and form a password-harvesting attack link with just a few clicks.
Highlights
- Straightforward, web-based user interface.
- No need to create templates all by yourself.
- Kismet makes accessibility easier.
- A beginner-friendly toolkit.
Give a try on these phishing tools and experience this phishing simulation software.
Phishing Frenzy
Email phishing campaigns are unbeatable with Phishing Frenzy. Thanks to Brandon “zeknox” McCann in 2013 for creating this open-source Ruby on Rails app. As a data harvester, you will initially need the Bing API key for proper function.
Yet, once you avail of it, your first 5000 transactions are completely free of charge. Phishing Frenzy now also has an Email Harvester that helps you enumerate specific mails throughout the web.
Highlights
- Best campaign management tool.
- Template reuse.
- Statistical generation.
- Having a domain name is not mandatory.
Give a try on these phishing tools and experience this phishing simulation software.
Gophish
Powered by a REST API, Gophish has a super cool user interface. The data is extractable even for scheduled events and timelines that include tracking email opens, submitted credentials, link clicks, and more. And the red team exercises work best for users and groups, sending profiles and landing pages.
However, besides these, Gophish can bypass filters and reach inboxes if you pick different ship profiles for various users.
Highlights
- Pixel-perfect phishing templates.
- Accustomed to business clients and partners.
- Full HTML editor.
- Cross-platform support – Windows, Mac OSX, and Linux.
Give a try on these phishing tools and experience this phishing simulation software.
Trending Phishing Tools for 2024 – Best Phishing Simulation Software
Acceptable for their features, but yet-to-be widespread, here comes the final set of phishing simulation software modules that we hope could be useful for your security research;
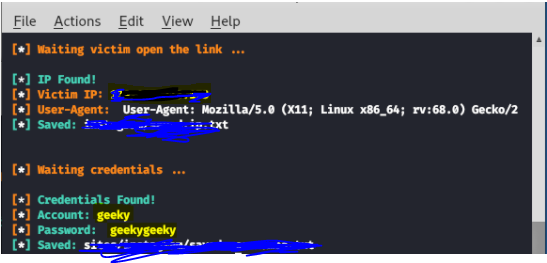
BlackEye
Since its foundation, Blackeye has worked across 38 global platforms, including Snapchat, Google, Instagram, Yahoo, PayPal, Spotify, Protonmail, GitHub, Protonmail, Twitch, Linkedin, etc. Hackers and credential harvesters have mostly preferred to use this tool through Kali Linux and Android via Termu. With ngrok introspectable tunnels, you can precisely execute a phishing assault, both outside and inside LAN.
Highlights
- 32 + 1 customizable templates.
- Stay connected with your target’s machine by port forward.
- Inbuilt arm support.
- Mobile version supported.
Give a try on these phishing tools and experience this phishing simulation software.
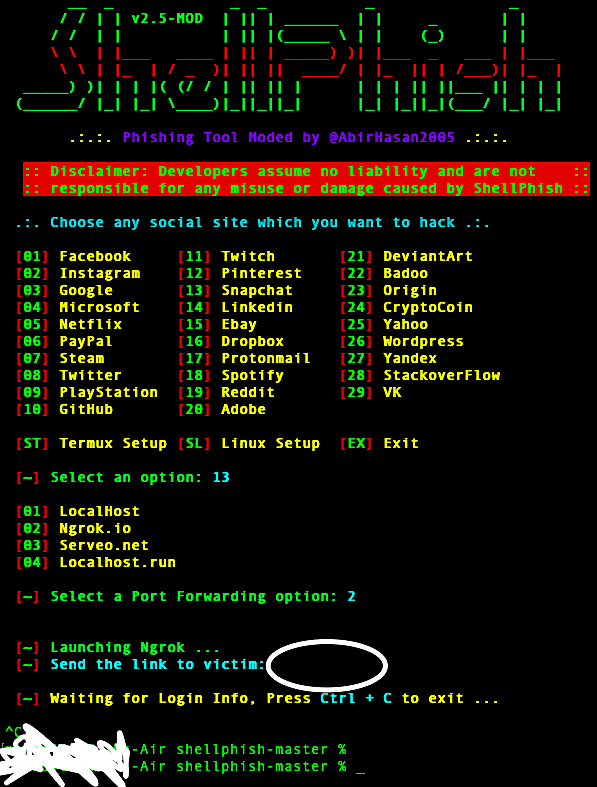
Shellphish
From Spotify and Dropbox to Reddit and DeviantArt, here’s another phishing simulation software, written by ‘thelinuxchoice.’ It hacks social media and related platforms. Once again, with ngrok, you can skip the hosting or port forwarding services.
This tool is gaining slow popularity with youngsters. And is best suited for data harvesting through WAN (Wide Area Network). Yet, the only con with Shellphish is that it cannot bypass the 2FA.
Highlights
- 18 general + 1 custom website.
- BASH language [Bourne-Again SHell].
- Easiest setup and installation.
- Strong Copyleft, GPL-3.0 License.
Give a try on these phishing tools and experience this phishing simulation software.
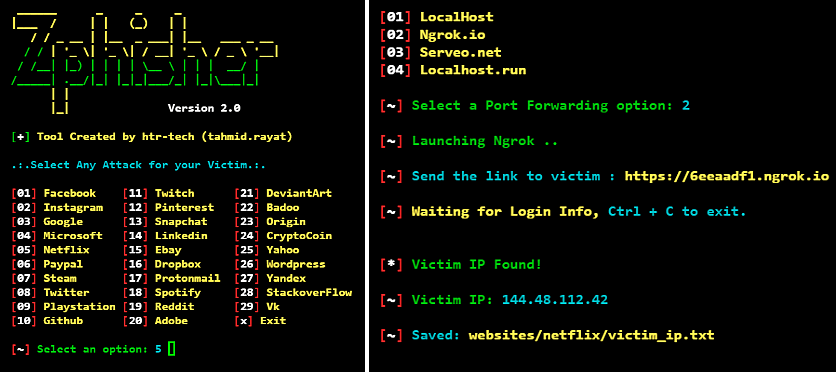
Zphisher
Did you know that Zphisher is an upgraded form of Shellphish? Yes. As one of the rarest phishing simulation tools so far, amateurs can utilize the best here, owing to its ease of usage and learnability. Indeed, you can even use this tool for generating an unlimited followers page.
However, you require multiple dependency packages, plus you need to update your pre-installed packages. And you are all set to hack 30+ sites.
Highlights
- 4 Port Forwarding Tools.
- Templates for regular social media and web pages.
- Lightweight (does not take extra space).
- Docker support
Give a try on these phishing tools and experience this phishing simulation software.
Conclusion
To this end, we would like to share the reality that there might be several other phishing simulation software programs online. But the takeaway is to use them only for educational purposes and stay ethical to yourself and your people. Rather than victimizing the general users, learn and get educated with these phishing tools. Stay secure and know how not to become a victim for another phisher shortly!
Subscribe to our newsletter for daily alerts on cyber events, you can also follow us on Facebook, Linkedin, and Twitter.
You can reach out to us via Twitter/ Facebook or mail us at admin@thecybersecuritytimes.com for advertising requests.
]]>The CVE-2023-38831 security flaw affects WinRAR versions before 6.23, enabling threat actors to create .RAR and .ZIP archives capable of executing background code for malicious purposes. The vulnerability has been exploited as a zero-day since April, primarily targeting cryptocurrency and stock trading forums.
It is to be noted that another advanced persistent threat (APT) group called GoldenJackal also has been engaging in espionage against government and diplomatic entities in Asia since 2019 and exhibited notable activity in Afghanistan, Azerbaijan, Iran, Iraq, Pakistan, and Turkey, as reported by cybersecurity firm Kaspersky.
Russian Hackers APT29’s Modus Operandi and Targeting
APT29 has been employing a BMW car sale lure to target embassy entities, using a malicious ZIP archive that executes a background script to display a PDF lure. The PDF then triggers the download of PowerShell code, leading to the execution of a payload.
The malicious archive, named “DIPLOMATIC-CAR-FOR-SALE-BMW.pdf,” has been used by APT29 to target multiple European countries, including Azerbaijan, Greece, Romania, and Italy. This phishing lure was previously employed in a campaign in May against diplomats in Ukraine.
Innovative Tactics: Ngrok for Communication
In a novel approach, APT29 has incorporated Ngrok, specifically its free static domains, for communication with the command and control (C2) server. This tactic allows the hackers to establish discrete rendezvous points, avoiding detection and enabling communication with compromised systems.
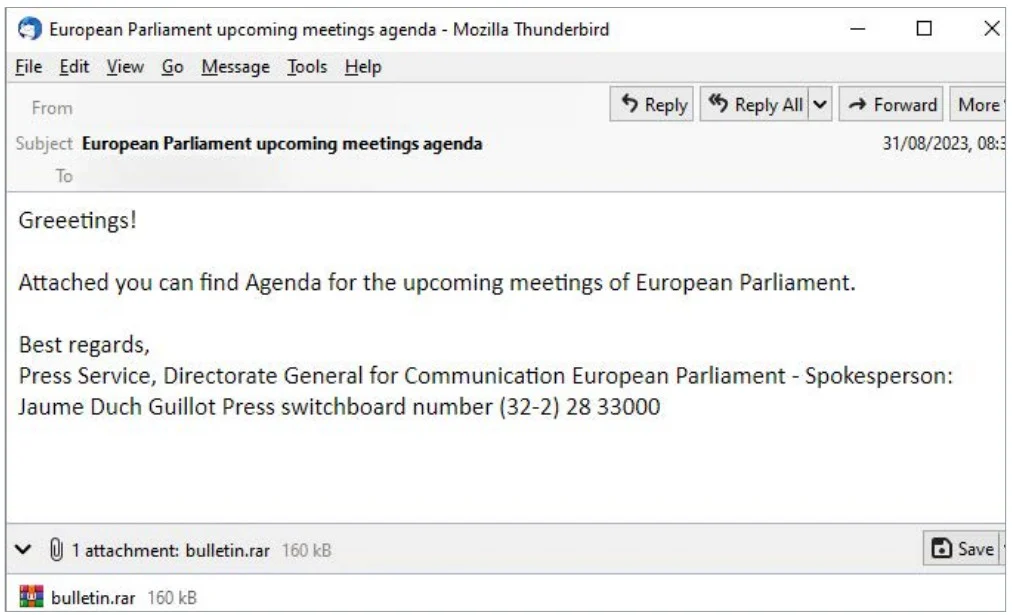
The Ukrainian National Security and Defense Council notes that APT29’s campaign stands out for its combination of old and new techniques. The WinRAR vulnerability is used to deliver payloads, while Ngrok services are employed to conceal communication with the C2 server.
Widespread Exploitation of WinRAR Vulnerability
Security researchers have observed the exploitation of the CVE-2023-38831 vulnerability by advanced threat actors, including APT28, who targeted political entities in the EU and Ukraine in a spearphishing campaign. Google’s October report highlighted its use by Russian and Chinese state hackers for stealing credentials and sensitive data.
The Ukrainian NDSC report provides a set of indicators of compromise (IoCs), including filenames, corresponding hashes for PowerShell scripts, an email file, domains, and email addresses associated with APT29’s cyberattacks.
]]>Boeing Data Breach Unveiled
LockBit ransomware successfully leaked over 43GB of files from Boeing after the aerospace company refused to comply with the ransom demands. Most of the data available on the hacker group’s leak site comprises backups for various systems, with the most recent backups timestamped as of October 22.
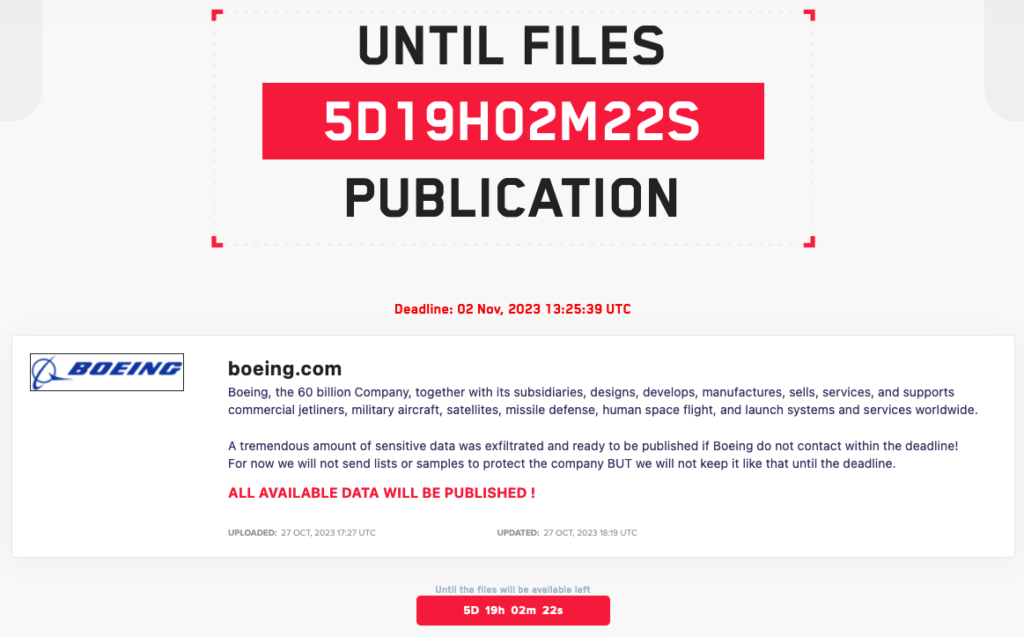
Deadline and Silence
On October 27, LockBit posted Boeing on their site and set a November 2nd deadline for the company to initiate negotiations. The hackers emphasized that they had acquired a substantial amount of sensitive data and were prepared to publish it. Although Boeing briefly disappeared from LockBit’s victim list, it reappeared on November 7, as the hackers declared that their warnings had gone unheeded.
Show of Force
With Boeing maintaining silence, the LockBit ransomware gang decided to exhibit their bargaining power. They threatened to release approximately 4GB of sample data, emphasizing that this was just a fraction of what they possessed. The hackers warned of publishing databases if positive cooperation from Boeing was not forthcoming.
Data Release and Speculation
On November 10, LockBit fulfilled its threat by releasing all the data it had obtained from Boeing. This included configuration backups for IT management software and logs for monitoring and auditing tools. The listing of backups from Citrix appliances sparked speculation about the potential use of the recently disclosed Citrix Bleed vulnerability (CVE-2023-4966), for which the exploit code was published on October 24.
Boeing’s Confirmation and LockBit’s Resilience
While Boeing acknowledged the cyberattack, the company refrained from providing details regarding the incident or how the hackers infiltrated their network. LockBit recognized as one of the most resilient ransomware-as-a-service (RaaS) operations, has been active for over four years, victimizing thousands across various sectors.
International Operations and Government Warnings
LockBit’s impact extends internationally, with victims including the Continental automotive giant, the UK Royal Mail, the Italian Internal Revenue Service, and the City of Oakland. In June, the U.S. government revealed that the gang had extorted approximately $91 million since 2020 through close to 1,700 attacks on various organizations. Additionally, in August, the Spanish National Police warned about a phishing campaign targeting architecture firms in Spain, aiming to encrypt systems using LockBit’s locker malware.
It is also to be noted that on September 2023, Ransomware group LockBit attacked Pelmorex Corp., the parent company of The Weather Network and on September 2021, Bangkok Airways was also a victim of the LockBit ransomware attack.
]]>Citrix Bleed Vulnerability: 1000s of Vulnerable Servers Detected
As of October 30, security organization Shadowserver identified over 5,000 vulnerable servers on the public internet. Additionally, GreyNoise observed 137 individual IP addresses attempting to exploit the Citrix vulnerability in the past week.
Patch Release and Persisting Challenges
Citrix acknowledged the issue and released a patch for the flaw, known as CVE-2023-4966, on October 10. However, merely applying the patch and rebooting the system isn’t sufficient, as session tokens continue to pose a risk. Experts warn that session tokens can be exploited even after patching, emphasizing the severity of the problem.
Ransomware Gangs Targeting the Vulnerability
The “mass exploitation” of this vulnerability has attracted the attention of at least two ransomware gangs, as of October 30. These criminals are distributing a Python script to automate the attack process, making it a significant threat. Essentially, this situation exposes a vulnerability reminiscent of 1998 in remote access solutions, and attackers are collecting session tokens like prized possessions.
Exploitation Across Multiple Sectors
Security firm Mandiant revealed that it is currently tracking four separate groups exploiting the vulnerability in various sectors, including legal and professional services, tech, and government agencies across regions such as the Americas, Europe, Middle East, Africa, and Asia-Pacific. The exploitation is widespread and affects numerous sectors.
Assessing Exploitation within Organizations
Mandiant identified various ways to check for exploitation within organizations’ networks. However, it’s crucial to understand that patterns of suspicious activity related to session hijacking may vary from one organization to another. Therefore, the outlined techniques might not be universally applicable or feasible.
Response from Cybersecurity Authorities
The US government’s Cybersecurity and Infrastructure Security Agency (CISA) added CVE-2023-4966 to its Known Exploited and Vulnerabilities Catalog. However, the vulnerability is still listed as “unknown” in the “used in ransomware campaigns” category, despite ongoing exploitation.
Corporate Data Theft and Financial Motivations
Criminals have been exploiting this vulnerability since late August, initially limited to cyber espionage. Mandiant Consulting CTO Charles Carmakal anticipates that other threat actors with financial motivations will increasingly exploit this flaw over time, highlighting the urgency of addressing the situation.
]]>This article delves into the ongoing Black Basta ransomware attack that has disrupted various aspects of TPL’s operations.
What is Black Basta Ransomware?
Black Basta Ransomware is a malicious software strain that has gained notoriety for its involvement in cyberattacks. This ransomware operation emerged in April 2022 and swiftly focused on targeting corporate victims through a double-extortion strategy. One of its early high-profile targets was the American Dental Association, where stolen data was leaked to exert pressure on victims.

Black Basta is known to collaborate with other cybercrime groups, such as the QBot malware operation, to gain initial access to corporate networks. Once inside, they employ tactics like stealing credentials and spreading laterally across the network while pilfering sensitive data. The threat actors typically deploy an encryptor throughout the compromised network, encrypting devices, and causing significant data loss.
Black Basta Ransomware and its Motives
The primary motivation behind this ransomware operation is financial gain. They often demand a ransom in exchange for a decryption key and the promise not to publish or sell the stolen data. Data theft plays a pivotal role in their extortion strategy, making victims more inclined to pay the ransom to protect their sensitive information from exposure.
The Black Basta gang is part of a broader landscape of ransomware attacks that continue to pose a significant threat to organizations worldwide. As cybercriminals become increasingly sophisticated, defending against such attacks necessitates robust cybersecurity measures and constant vigilance.
Impact of the Cyberattack on TPL’s Services
Earlier this week, TPL reported a ransomware attack that has inflicted substantial technical outages on its websites and online services.
This section details the specific services affected, including the unavailability of the tpl.ca website, issues with accessing online accounts, and disruptions in tpl: map passes and digital collections services. Public computers and printing services have also been rendered inaccessible due to the attack.
Black Basta Ransomware: Response and Investigation Efforts
Despite the significant disruption caused by the Black Basta ransomware attack, TPL assures its staff and customers that there is no evidence of compromised personal information.
This subheading focuses on the library’s response to the incident, mentioning its collaboration with law enforcement and third-party cybersecurity experts. The article also highlights TPL’s proactive measures to address the situation and its estimated timeline for restoring normal operations.
Black Basta Ransomware Operation
The article concludes by shedding light on the perpetrators behind the ransomware attack, identifying the Black Basta ransomware operation as the source.
It provides insights into the history and modus operandi of this ransomware gang, emphasizing the importance of vigilance against such cyber threats.
]]>The attacker claims to have obtained the source code for D-Link’s D-View network management software and millions of records containing personal information of customers and employees, including details about the company’s CEO. The stolen data encompasses names, emails, addresses, phone numbers, account registration dates, and the users’ last sign-in dates.
D-Link Data Breach results in theft of Personal Data and Source Code
The threat actor presented 45 stolen records, dating between 2012 and 2013, to validate the breach. Notably, the data appeared outdated.
The attacker revealed, “I have breached the internal network of D-Link in Taiwan, I have 3 million lines of customer information, as well as source code to D-View extracted from the system. This does include the information of MANY government officials in Taiwan, as well as the CEOs and employees of the company.”
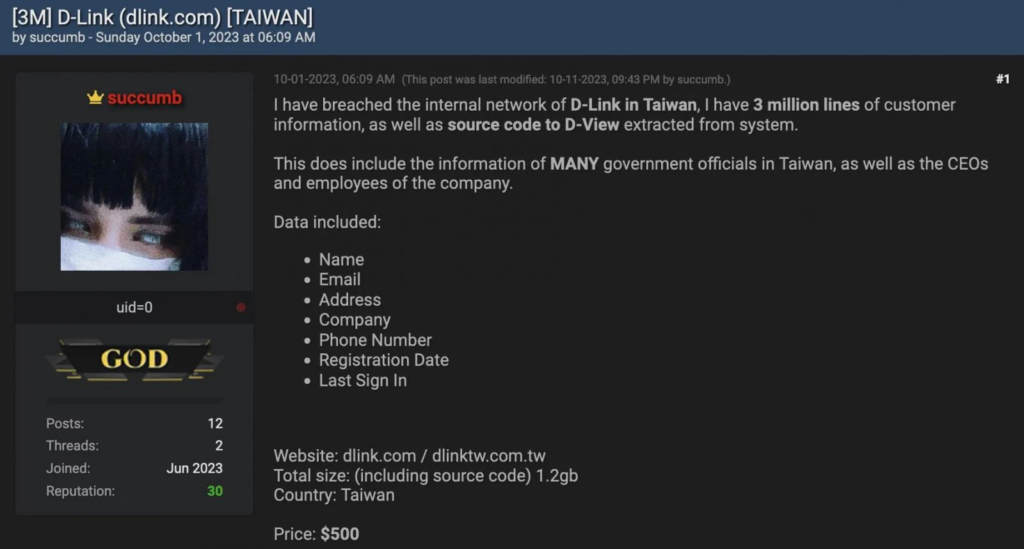
The compromised data has been available for purchase on the hacking forum since October 1st, with the threat actor demanding $500 for the stolen customer information and the alleged D-View source code.
D-Link has attributed the security breach to an employee falling victim to a phishing attack, which provided the attacker access to the company’s network.
In response, the company swiftly shut down potentially affected servers and disabled all but two user accounts used during the investigation.
While confirming the breach, D-Link clarified that the intruder accessed a product registration system within a “test lab environment,” operating on an outdated D-View 6 system that reached its end of life in 2015.
Breach Details, Company Response, and Minimal Impact on Customers
The reason for keeping an end-of-life server operational on D-Link’s network, potentially exposed to the internet for seven years, remains uncertain.
Contrary to the attacker’s claim of stealing millions of users’ data, D-Link revealed that the compromised system contained approximately 700 records, pertaining to accounts that had been inactive for at least seven years.
The company stated, “Based on the investigations, however, it only contained approximately 700 outdated and fragmented records that had been inactive for at least seven years.” Most of the data comprised low-sensitivity and semi-public information.
D-Link also suspects that the threat actor intentionally manipulated recent login timestamps to create the illusion of a more recent data theft. Additionally, the company reassured that the majority of its existing customers are unlikely to be affected by this incident.
]]>The Israel-Palestine Cyber Conflict, a turbulent and evolving facet of the longstanding regional conflict, has surged to prominence in recent times. Amidst the physical clashes between Israel and Hamas, various hacktivist groups have ignited a parallel digital war.
This article explores the multifaceted landscape of this cyber confrontation, delving into the motives, tactics, and impacts of various hacktivist factions. From Anonymous Sudan’s swift response to Hamas’ rocket attacks to the disruption of critical infrastructure by Cyber Av3ngers, and the global rallying cry of the Ghosts of Palestine, the digital frontlines have become a pivotal arena in this complex conflict.
Escalation of the Israel-Palestine Cyberwarfare
As the Israel-Hamas conflict escalated over the weekend following a major attack by the Palestinian militant group, it wasn’t just traditional warfare that took center stage. In the shadows, a growing number of hacker groups joined the fray, unleashing a wave of disruptive cyberattacks.
Hacktivist Groups Take Aim in the Israel Cyberattack
While both state-sponsored actors and hacktivist groups supporting various sides intensified their cyber efforts, one group, in particular, Anonymous Sudan, wasted no time. Less than an hour after Hamas fired its first rockets, they launched their first hacktivist attacks against Israel. Their targets included emergency warning systems, crippling alerting applications across the country.
Cyber Frontlines: Disruption and Defacement
Cyber Av3ngers, a pro-Hamas group, struck at the heart of Israel’s infrastructure, targeting the Israel Independent System Operator (Noga) and claiming to compromise its network and website. They also went after the Israel Electric Corporation and a power plant, causing significant disruption. Meanwhile, Killnet, a notorious pro-Russian group, aimed its cyber arsenal at Israeli government websites.
Ghosts of Palestine
The Ghosts of Palestine, a Palestinian hacker gang, rallied hackers worldwide to launch attacks on private and public infrastructure in Israel and the United States. Libyan Ghosts entered the fray by defacing small Israeli websites in support of Hamas.
Most of these hacktivists employed distributed denial-of-service (DDoS) attacks to wreak havoc, although their claims of causing significant disruption should be taken with a grain of caution. However, groups like Killnet and Anonymous Sudan, both with ties to Russia, have a history of executing highly disruptive attacks on major companies.
Pro-Israel group ThreatSec retaliated by claiming to compromise Gaza-based ISP AlfaNet’s infrastructure, while hackers allegedly operating from India attacked Palestinian government websites, rendering some inaccessible. Garuna pledged its support for Israel, and TeamHDP targeted the websites of Hamas and the Islamic University of Gaza.
More hackers target Israel organizations
In a recent report, Microsoft noted an uptick in activity from a Gaza-based threat group named Storm-1133, focusing on Israeli organizations in defense, energy, and telecommunications sectors. Microsoft believes this group is working to further the interests of Hamas.
The Jerusalem Post has been targeted by multiple cyberattacks this morning causing our site to crash.
— The Jerusalem Post (@Jerusalem_Post) October 8, 2023
We'll be back soon and will continue to be the top source of information on Operation Swords of Iron and the murderous attacks by Hamas. pic.twitter.com/6S2GOl6Wma
As the conflict raged on, even as Israel carried out retaliatory air raids into Hamas hideouts, cyberattacks targeted the country’s leading English newspaper, “The Jerusalem Post,” causing multiple site crashes. Amid this digital battlefield, the newspaper vowed to remain a vital source of information on the ongoing Operation Swords of Iron and Hamas’ attacks.
The toll from the conflict continued to mount, with The Times of Israel reporting a rising number of injured from Hamas attacks, including gravely injured individuals. As Israel launched “Operation Swords of Iron” in response to the incursion, the situation remained fluid, with both sides grappling not only on the ground but also in the digital realm.
]]>This advisory also delves into the tactics, techniques, and procedures (TTPs) employed by threat actors to exploit these misconfigurations, with objectives ranging from gaining access to sensitive information to targeting vital systems.
The valuable insights presented in this report have been gathered through rigorous assessments and incident response activities conducted by the Red and Blue teams of both agencies. These evaluations span a wide spectrum, including the networks of the Department of Defense (DoD), Federal Civilian Executive Branch (FCEB), state, local, tribal, and territorial (SLTT) governments, as well as the private sector.
The discoveries made during these assessments underscore the alarming prevalence of common misconfigurations, such as default credentials, service permissions, and configurations of software and applications.
Other notable vulnerabilities include improper separation of user/administrator privilege, insufficient internal network monitoring, poor patch management, and the bypassing of system access controls.
Top 10 Cybersecurity Misconfigurations
Eric Goldstein, Executive Assistant Director for Cybersecurity at CISA, emphasized the gravity of these misconfigurations, stating that they place every American at risk. The top ten misconfigurations highlighted by NSA and CISA’s teams are as follows:
- Default configurations of software and applications
- Improper separation of user/administrator privilege
- Insufficient internal network monitoring
- Lack of network segmentation
- Poor patch management
- Bypass of system access controls
- Weak or misconfigured multifactor authentication (MFA) methods
- Insufficient access control lists (ACLs) on network shares and services
- Poor credential hygiene
- Unrestricted code execution
As elucidated in the joint advisory, these common misconfigurations reveal systemic vulnerabilities within the networks of numerous large organizations. This emphasizes the crucial need for software manufacturers to adopt secure-by-design principles to mitigate the risk of compromise.
You can learn from NSA’s experience working Red and Blue team engagements. Bad actors will look for easy opportunities to exploit vulnerabilities and compromise networks. Here are the top 10 cybersecurity misconfigurations we see:l along with @CISAgovhttps://t.co/in63ZwXCTs pic.twitter.com/P1Low2GRBk
— Rob Joyce (@NSA_CSDirector) October 5, 2023
Rob Joyce, a prominent figure in the field of cybersecurity, endorsed the call for proactive practices among software manufacturers. These practices include integrating security controls into the product architecture from the initial stages of development and throughout the software development lifecycle.
Furthermore, the discontinuation of default passwords and safeguarding individual security controls to prevent the compromise of entire systems is vital. Eliminating whole categories of vulnerabilities, such as adopting memory-safe coding languages and implementing parameterized queries, is also advocated.
Goldstein stressed the importance of mandating multifactor authentication (MFA) for privileged users and making it a standard practice, rather than an optional choice.
To counter these common misconfigurations, NSA and CISA advise network defenders to implement several recommended mitigation measures, including:
- Eliminating default credentials and hardening configurations
- Deactivating unused services and implementing stringent access controls
- Ensuring regular updates and automating the patching process, with a focus on known vulnerabilities that have been exploited
- Reducing, restricting, auditing, and closely monitoring administrative accounts and privileges
In addition to these measures, NSA and CISA encourage organizations to test and validate their security programs against the threat behaviors mapped to the MITRE ATT&CK for Enterprise framework. The two federal agencies also recommend testing existing security controls inventory to assess their effectiveness against the ATT&CK techniques outlined in the advisory.
]]>